
January 06, 2025
🥖 Palette Cleanser
Some people may choose to start the new year with a diet or solemn vow to go to the gym. Not Volkswagen. Instead of going on a diet Volkswagen has the honor of being the first AWS-related data breach disclosure of 2025. Apparently "the breach has been attributed to an Amazon cloud storage system misconfiguration", which reads suspiciously like "oops, exposed S3 bucket".
Ten years ago securing S3 buckets was hard because there weren't easy ways to identify and prevent accidental bucket exposure. Today, securing buckets is hard because there are way more buckets and way more reasons to make them public on purpose, like being empty or hosting a website. Who’s to say if any of the up to one million buckets in your account shouldn't be public?
Here are just some of the risk factors cloud security tools like Plerion evaluate before flagging a bucket as a risk.
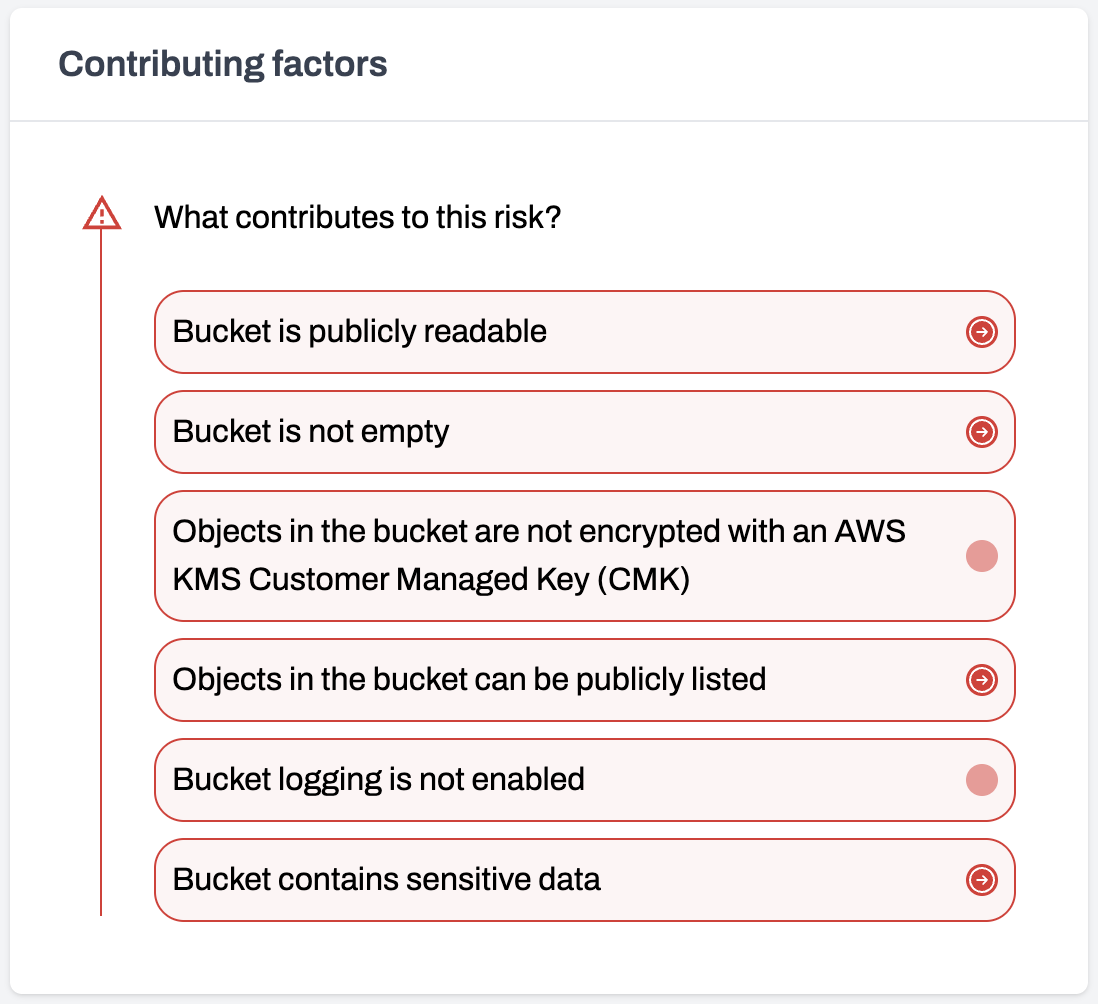
Enjoy the first issue of 2025, it's surprisingly 🔥🔥🔥.
Have feedback about AWS Security Digest? Tell us here. This issue is also available to share online.
📋 Chef's selections
-
Hat Trick: AWS introduced same RCE vulnerability three times in four years by Giraffe Security
Don't be confused about dependency confusion. Simple bugs are the best bugs and this is a must-read story about a beautifully simple bug, seasoned with some shared responsibility fail. AWS published some python libraries in a private registry along with instructions on how to install them using pip using an "extra index". Only the extra index was checked AFTER the default registry so attackers could just register fake malicious packages in the default registry. Genius.
Summary videos are back, starting with this one.
-
Avoiding mistakes with AWS OIDC integration conditions by Scott Piper
One way to secure the cloud is to educate all the users of cloud how not to do the bad things. Another way is to educate the vendors who support users of cloud. In this predictably thorough article Scott reviews how 24 vendors document their AWS OIDC integrations and teaches them how to avoid leading their users to catastrophic failure. If you integrate your AWS environment with Github, Bitbucket, Vercel, or similar, this is worth a browse.
-
Deep Dive: AWS Organization Policies (Part 1) by Naman Sogani
There's been A LOT of control policy content since AWS launched resource control policies (RCP) at re:Invent 2024. You might be sick of it but you might want to consider swallowing hard and reading this write up because it's (excruciatingly) detailed. Naman focuses on how to combine SCPs and RCPs to control access, enforce security requirements, and lay the foundations for a well-defined data perimeter.
Bonus: Centralized Root Access in AWS: A Game-Changer for LandingZone security and Combine AWS WAF with reactive infrastructure to block attackers (and don't go broke in the process)
🥗 AWS security blogs
🍛 Reddit threads on r/aws
🤖 Dessert
Dessert is made by robots, for those that enjoy the industrial content.
🧁 IAM permission changes
🍹 IAM managed policy changes
- AWSElasticDisasterRecoveryConsoleFullAccess_v2
- AWSElasticDisasterRecoveryServiceRolePolicy
- ComputeOptimizerServiceRolePolicy
- AWSQuicksightAthenaAccess
- AmazonAthenaFullAccess
- SageMakerStudioProjectProvisioningRolePolicy
- SageMakerStudioProjectUserRolePermissionsBoundary
- SageMakerStudioProjectUserRolePolicy
- ReadOnlyAccess
- SecurityAudit
☕ CloudFormation resource changes
-
No resource updates this week.
🎮 Amazon Linux vulnerabilities
📺 AWS Security Bulletins
-
No bulletins this week.