
Sponsor
New Blog! 5 Advantages of Securing Cloud Infrastructure with Teleport and AWS Identity Federation
This time, learn about the advantages of easily controlling who can provision and access your critical AWS resources:
- Fine-grained control of each AWS service
- Consistent experience in using AWS Console and CLI
- Simplified role-based access control
- JIT elevated privileges
- Insights through AWS CloudTrail and Teleport Audit
In a nutshell
Re:Invent 2022 is coming in just a few days now, there is already a lot of movements in November's pre:Revent. I will, with many contributors update this one-pager with all relevant new AWS services and updated services. Stay connected, Folks.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSBackupDataTransferAccess
- AWSBackupFullAccess
- AWSBackupOperatorAccess
- AWSBackupRestoreAccessForSAPHANA
- AWSBackupServiceLinkedRolePolicyForBackup
- AWSBackupServiceRolePolicyForBackup
- AWSResourceExplorerFullAccess
- AWSResourceExplorerReadOnlyAccess
- AmazonEventBridgeFullAccess
[...]


🗒️ A Dive Into Web Application Authentication
@jameschiapet discusses:
* The difference between authentication and authorization
* Why we need MFA
* How "sign in with" works
* SSO
* Passwordless authentication
* API authentication
* Deep links
betterappsec.com/a-medium-dive-…
 92
92 41Nov 08 · 7:00 PM
41Nov 08 · 7:00 PM
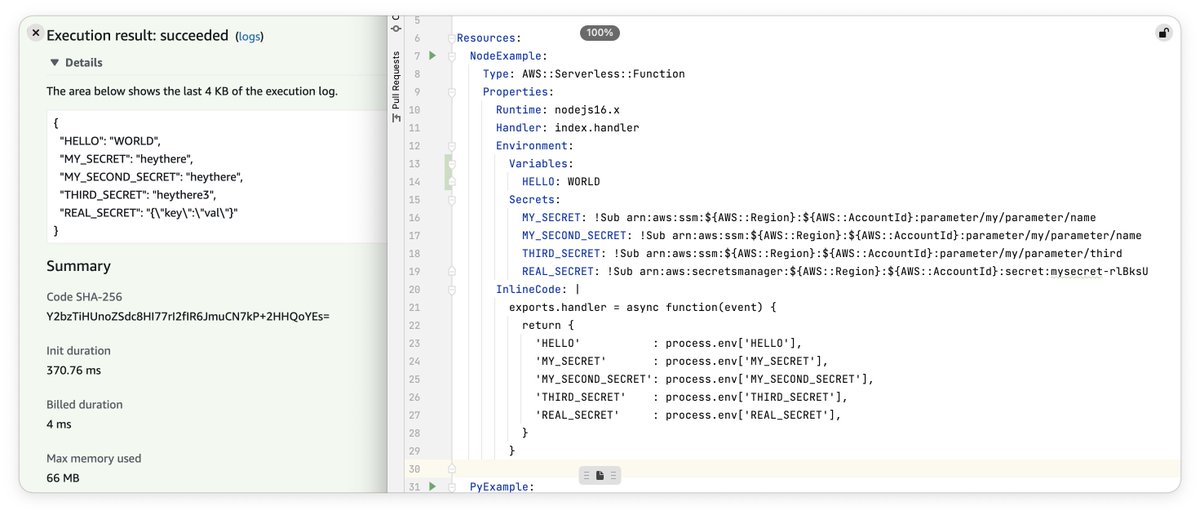
A while ago I tweeted about how secrets could be populated as env vars in Lambda. @theburningmonk said it would be preferable if secrets were available via the function handler context. So I built a proof-of-concept of that. Try guess how it works!
github.com/aidansteele/se…
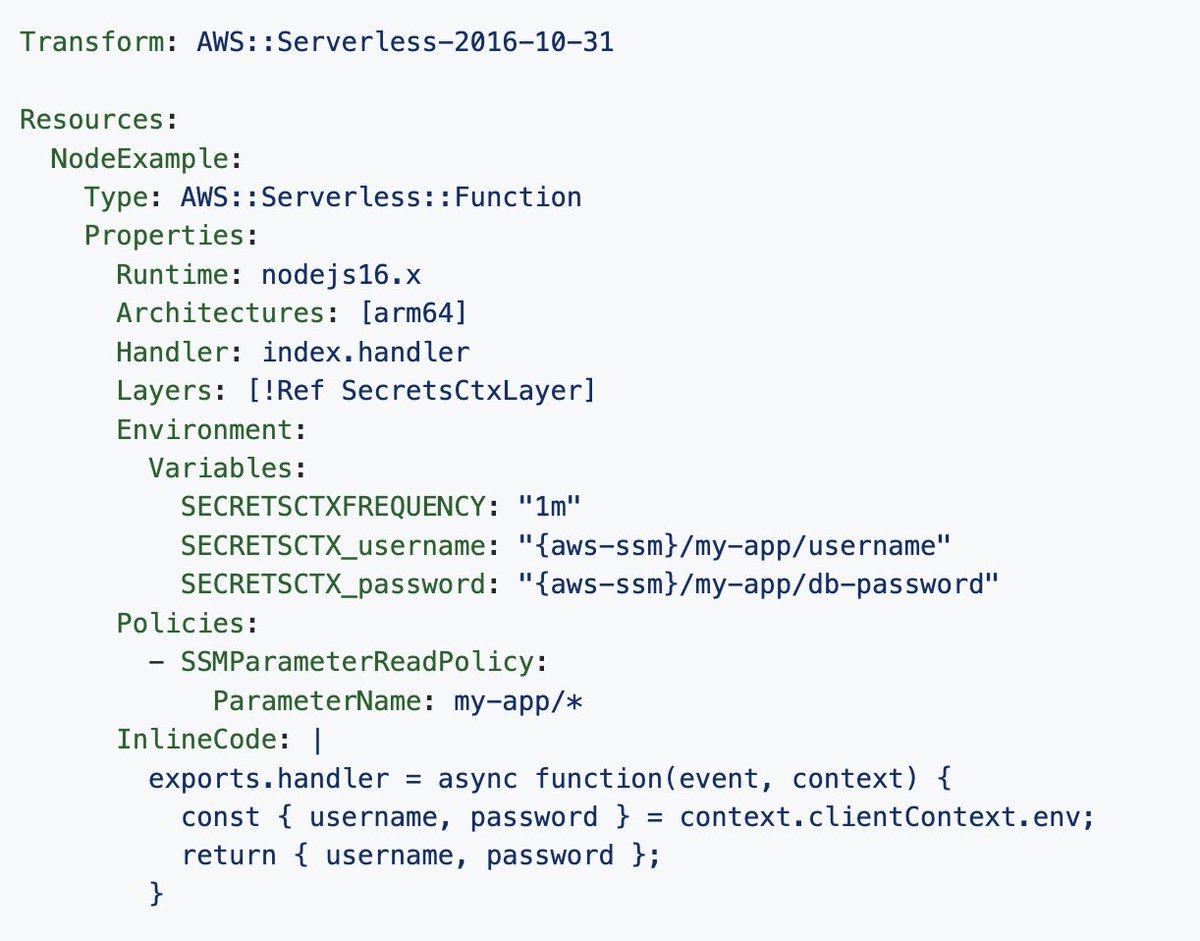

The recent launch from AWS of a new way to access secrets from Lambda got me thinking.
Specifically thinking "I should stop complaining every six months on Twitter and demonstrate how I think it is should work". So here's a blog and Github repo.
awsteele.com/blog/2022/10/1…
 115
115 17Nov 13 · 3:35 AM
17Nov 13 · 3:35 AM
I do look at lines of code and number of commits by engineer. Mostly to see if they might need a break from organizational wrangling and find some space to code again and if I can help with that. It's always a good reminder for me to code more too.
 129
129 3Nov 07 · 7:30 PM
3Nov 07 · 7:30 PM
Make it free you cowards.

We apologize to those who have been served a misleading message from a fake Lilly account. Our official Twitter account is @LillyPad.
 82
82 3Nov 11 · 8:13 PM
3Nov 11 · 8:13 PM
Well this is freakin’ awesome
aws.amazon.com/blogs/compute/…
 74
74 7Nov 11 · 12:45 AM
7Nov 11 · 12:45 AM
guys get it together twitter.com/TwitterSupport…

We’re not currently putting an “Official” label on accounts but we are aggressively going after impersonation and deception.
 68
68 4Nov 11 · 5:17 AM
4Nov 11 · 5:17 AM
I've just booked a trip to re:Invent... and discovered nearly all sessions are full. 😭 I'm going to be wandering around. My DMs are open if anyone wants to meet up!
 60
60 1Nov 08 · 6:01 PM
1Nov 08 · 6:01 PM
Still waiting for the Senate results from D.C., Puerto Rico, and Guam.
 54
54 5Nov 09 · 3:08 PM
5Nov 09 · 3:08 PM
I empathize with software vendors using the SSO Tax - Single-Sign-On costs money to implement, it ain't free, & it drives sales
But it's fucking ridiculous to expect companies to pay $600 PER USER/month just to get SAML. That's a real quote from a vendor
Looking at you, @vercel
 56
56 3Nov 08 · 8:03 PM
3Nov 08 · 8:03 PM
Just your semi-regular reminder that if you work with AWS IAM, you should be taking advantage of @iann0036's permissions.cloud reference for a clear, user-friendly way to navigate the different service API methods and actions
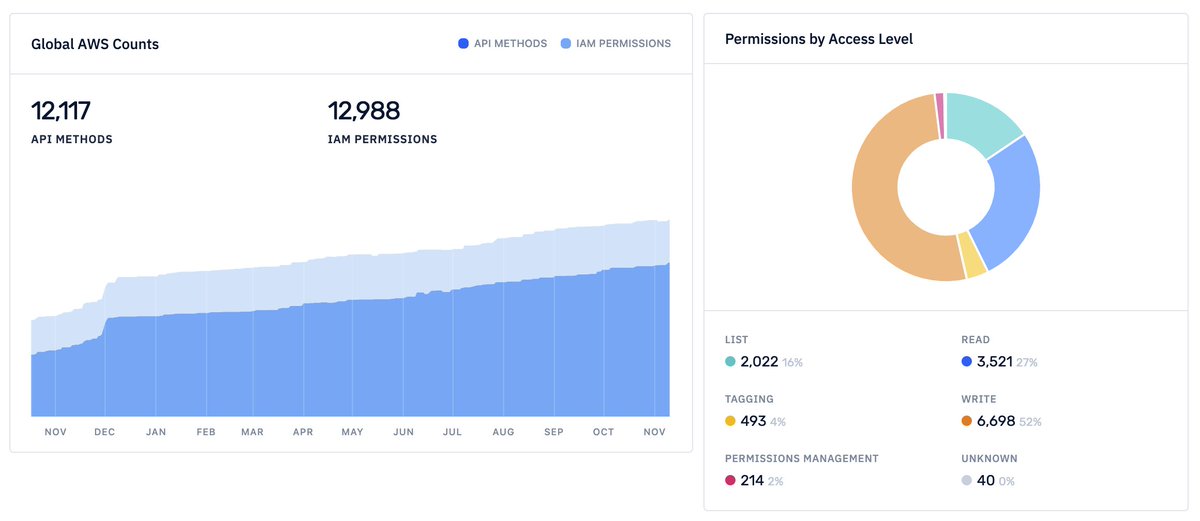
 39
39 6Nov 11 · 1:02 AM
6Nov 11 · 1:02 AM- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email













