
Sponsor
ProwlerPro is the most comprehensive, free tool for AWS security.
ProwlerPro is trusted by orgs of all sizes, and used everyday so teams can be confident in their AWS security framework. Everything you love about Prowler Open Source plus:
- Parallelized processing for faster results
- Dashboards with actionable, direct insights for every level of detail of your security posture
- Holistic view of your infrastructure for any AWS region
- Answers in minutes
Use ProwlerPro free today, and see what your first scan can do.
In a nutshell
We are all trying to enhance our AWS Security posture, reduce our attack surface, prevent AWS hijacking, or comply with our preferred CISO and certification authorities.
A starting point is to identify AWS assets, and it could be a difficult task for unknown AWS accounts, and large environments using multiple AWS Regions.
Fortunately, this blog post will show you different techniques to list your AWS assets.
I really like the one that is using AWS Cloud Control API.
I'll add another one by using a new prowler command (beta): prowler -i
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSConfigServiceRolePolicy
- AWSFMAdminFullAccess
- AWSOrganizationsFullAccess
- AWSOrganizationsReadOnlyAccess
- AWSSSODirectoryAdministrator
- AWSSSOMasterAccountAdministrator
- AWSSSOMemberAccountAdministrator
- AWSSSOServiceRolePolicy
- AWSSystemsManagerAccountDiscoveryServicePolicy
- AWS_ConfigRole
[...]
Sponsor
By using AWS cloud, your team is experimenting, launching instances, databases, and data modeling tools, and the typical behavior is to forget to turn off things. It's natural.
To get rid of this, to be aware of what I've let running. I've built a saas product called unusd.cloud – for me, for students, cloud practitioners, and for your DevOps teams.
It's free for a single AWS account (forever)

Happy birthday AWS IAM policy language! 10 years old for the current version, with the original being from 2008-10-17.
 253
253 49Oct 17 · 6:10 PM
49Oct 17 · 6:10 PM
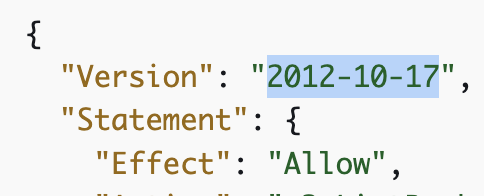
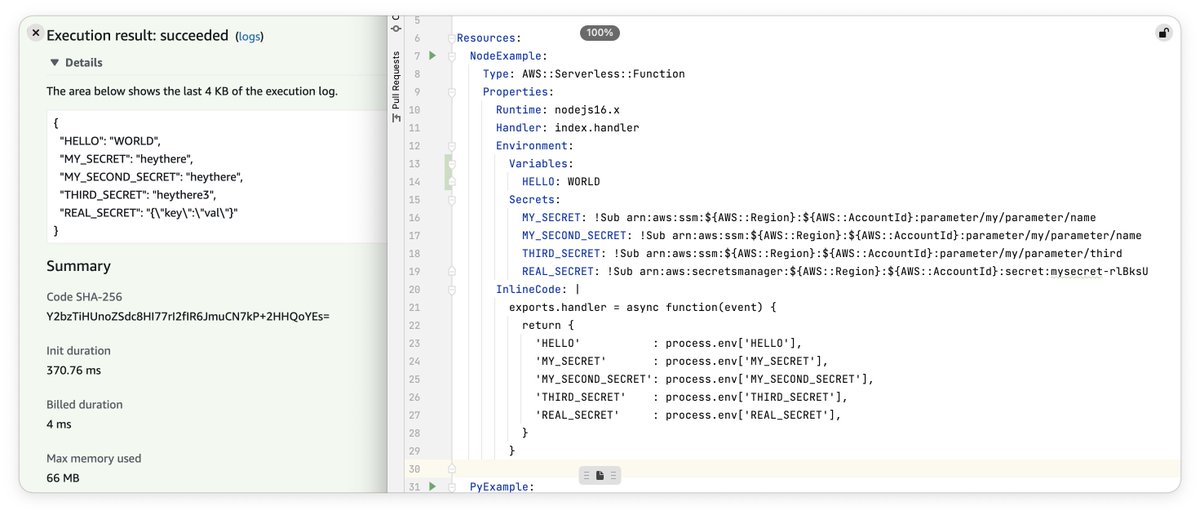
The recent launch from AWS of a new way to access secrets from Lambda got me thinking.
Specifically thinking "I should stop complaining every six months on Twitter and demonstrate how I think it is should work". So here's a blog and Github repo.
awsteele.com/blog/2022/10/1…
 165
165 19Oct 20 · 10:46 AM
19Oct 20 · 10:46 AM
Seattle voters, please vote for ranked choice voting (RCV), that's prop 1B, and please retweet for reach! I've voted in Ireland using it and seen its benefits in action, and the @LWV agree that it's the best option on the ballot! Here's five reasons and more info ...
 125
125 55Oct 23 · 10:54 PM
55Oct 23 · 10:54 PM
🐦 Cloned Website Token
Detect targeted phishing attempts by placing a canary token in the JavaScript on your websites
Notifies you if someone clones your site and hosts it on another domain
By @ThinkstCanary
docs.canarytokens.org/guide/cloned-w…
 82
82 23Oct 18 · 5:00 PM
23Oct 18 · 5:00 PM
🛡️ @MetloHQ
An open-source API security platform
Endpoint Discovery - Scans network traffic and creates an inventory of every API
Scans endpoints for PII & gives a risk score
Alert on unauth endpoints returning sensitive data, Open API spec diffs
github.com/metlo-labs/met…
 70
70 28Oct 19 · 11:55 PM
28Oct 19 · 11:55 PM
How can Apple have updated their TV remote but still not added "Find Me"? This has got to be the most obvious missing feature! Being able to chirp the remote from a paired phone or watch would be a living room game changer. Do the design team not own couches? twitter.com/i/web/status/1…
 86
86 4Oct 18 · 9:51 PM
4Oct 18 · 9:51 PM
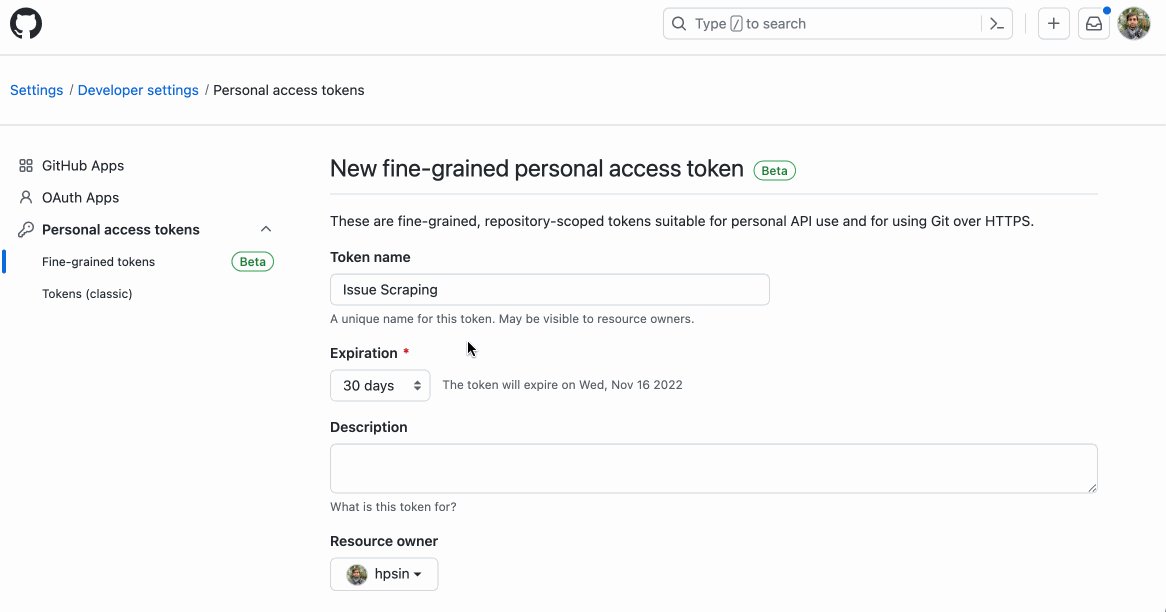
GitHub released fine-grained Personal Access Tokens (PATs)!🎉
Before this, classic PATs would have the same set of privileges as the user
Thank god. No more creating machine users with sorta god-mode PATs or SSH keys just to clone private Git submodules
github.blog/2022-10-18-int…
 49
49 13Oct 22 · 1:56 AM
13Oct 22 · 1:56 AM
Absolutely no way this could go wrong 🙃

Software to Fix Biased Performance Reviews That Hinder Women and People of Color bloomberg.com/news/articles/…
 43
43 2Oct 18 · 1:38 AM
2Oct 18 · 1:38 AM
Found a pic of me presenting on AWS 8yrs ago today. They’ve since added:
+17 Regions
+61 Availability Zones
+361 Edge locations
What a ride it was being on the inside as AWS grew so fast 🚀
Now I get to see it from the customer side. Still just as excited for what’s next!

 42
42 0Oct 22 · 10:04 PM
0Oct 22 · 10:04 PM
Are there alternatives to AWS Kinesis that work basically the same as Kinesis, but support more than 1MB/sec per shard?
 35
35 3Oct 23 · 12:30 AM
3Oct 23 · 12:30 AMAnnouncement: https://aws.amazon.com/about-aws/whats-new/2022/10/dark-mode-support-aws-management-console/
Looks pretty good too, just tried it out
tl;dr; Is using separate developer AWS accounts with "cloud" development environments to replace local environments a viable solution, or is that just a thing people do in tech demos / only a good theoretical idea?
I'm at a point on a project where I'm starting to loose the battle of …
I've used AWS for nearly four years -- I have several certs and I think I grasp most IAM concepts. But I would be lying if I told you I grasp all the concepts especially around assumption/passing of roles, STS service, boundaries etc IAM is like this black box that …
- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email










