
Sponsor - Secure your Cloud Infrastructure with Teleport and AWS IAM
Join Teleport for the webinar on October 13th and learn about the challenges in securely delegating access to your AWS resources. Save your spot to find out:
- How companies are currently managing their AWS infrastructure
- Integrating Teleport Access Plane with AWS IAM
- The top 5 advantages of using Teleport to access AWS resources
In a nutshell
An important change in AWS IAM Role Trust Policy: TL;DR
- BEFORE: Roles implicitly trusted themselves from a role trust policy perspective if they had identity-based permissions to assume themselves.
- NOW: Role trust policy must explicitly grant permission to all principals, including the role itself.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSApplicationMigrationAgentInstallationPolicy
- AWSApplicationMigrationAgentPolicy
- AWSDataLifecycleManagerServiceRole
- AWSDeviceFarmServiceRolePolicy
- AWSIoTFleetwiseServiceRolePolicy
- AmazonFSxConsoleFullAccess
- AmazonFSxConsoleReadOnlyAccess





I regret to inform that I am extremely back on my bullshit.
I've been thinking about connectivity in unusual places. And I got to thinking: can I establish bidirectional connectivity over the Internet between two EC2 instances in private subnets without a third-party relay?
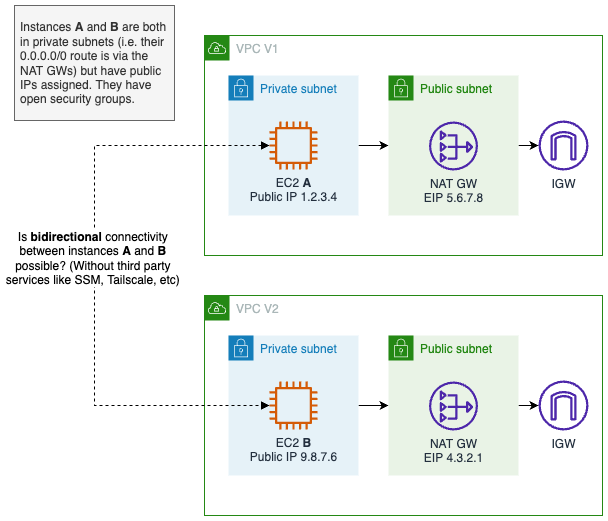
 364
364 49Sep 22 · 3:00 AM
49Sep 22 · 3:00 AM
Are you serious Oracle? A cross tenant vulnerability in OCI where you could just specify the disk ID of another customer on compute boot & it would attach to yours? That’s fucking unreal
Congrats to Wiz on another great finding. But Jesus Christ that’s such a bad look for Oracle

Vulnerability full disclosure - New Oracle cloud vulnerability allowed users to access the virtual disks of other Oracle customers >>
 129
129 34Sep 20 · 4:40 PM
34Sep 20 · 4:40 PM
🌩️ PenTesting.Cloud
Free cloud-focused security challenges
* Bypassing IMDSv2 meta-data controls
* S3 buckets
* Leaky CloudFormation templates
#Pentesting
pentesting.cloud
 119
119 42Sep 20 · 9:00 PM
42Sep 20 · 9:00 PM
BGP hijack of AWS IPs on August 17 to steal cryptocurrency.
AFAIK this is the 3rd BGP hijack against AWS to steal cryptocurrency.
- 2014 secureworks.com/research/bgp-h…
- 2018 arstechnica.com/information-te…
Info on AWS's work to stop BGP hijacks from 2021: aws.amazon.com/blogs/networki…

Must-read report from @coinbase that explains what last month's BGP hijack against Amazon was all about: a front-end hijack attack against Celer Bridge resulting in 32 victims and $235k in crypto losses.
And @kentikinc's view of the hijack route:
twitter.com/DougMadory/sta…
 83
83 41Sep 24 · 3:10 PM
41Sep 24 · 3:10 PM
Here's the GitHub link, but I swear to god if anyone deploys this to production I'm going to cry - and then buy you all the drinks in the world at re:invent.
github.com/aidansteele/ma…
 77
77 6Sep 22 · 3:00 AM
6Sep 22 · 3:00 AM
Even Republican Senator Mike Lee calls this what it is ... racism. What Indian and Chinese immigrants have to deal with is especially insane. We badly need a more functioning immigration system in the US.

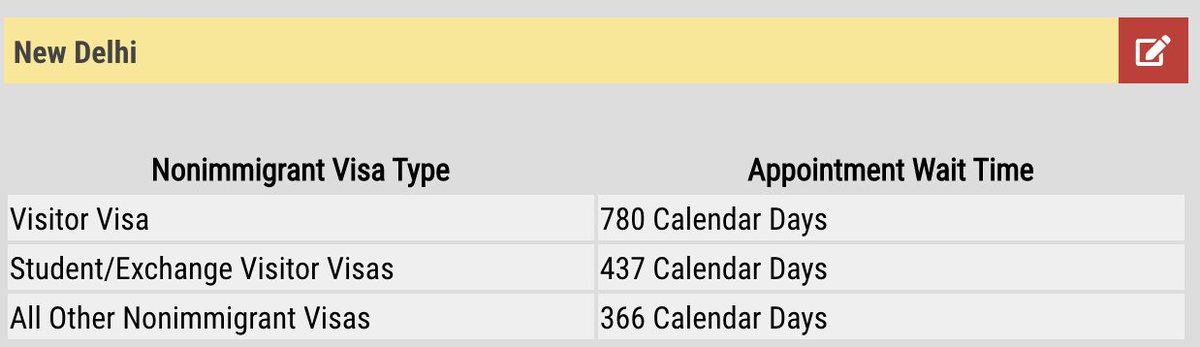
1/9 Indians in the US on a work visa can't go home. There’s NO appointments.
The now ~200k H-1B Telegram group is growing by 13,000 per month.
Even with ~$40m in fees, the 5 VACs process ~10,000 a month. The next availability is ~2024!
Here’s 6 stories from hurting families:
 56
56 10Sep 24 · 11:08 AM
10Sep 24 · 11:08 AM
Lazy twitter, someone please put together a list of thematic breach lists (a list of lists). Examples:
- magoo.github.io/Blockchain-Gra…: crypto currency hacks
- cloudvulndb.org: Cloud provider security incidents
- github.com/ramimac/aws-cu…: AWS customer security incidents
 49
49 12Sep 19 · 6:12 PM
12Sep 19 · 6:12 PM
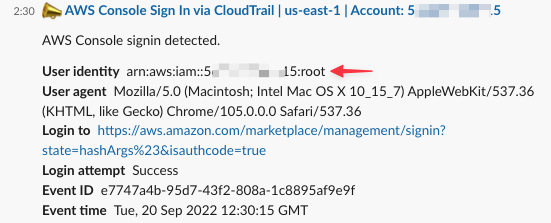
🆕 AWS Security Survival Kit: Bare minimum AWS Security Alerting on:
1. Root User activities
2. CloudTrail changes
3. AWS Personal Health Events
4. IAM Users changes
5. MFA updates
6. Unauthorized Operations
7. Failed AWS Console login authentication
👉🏻 github.com/zoph-io/aws-se…
 49
49 10Sep 20 · 5:00 PM
10Sep 20 · 5:00 PM
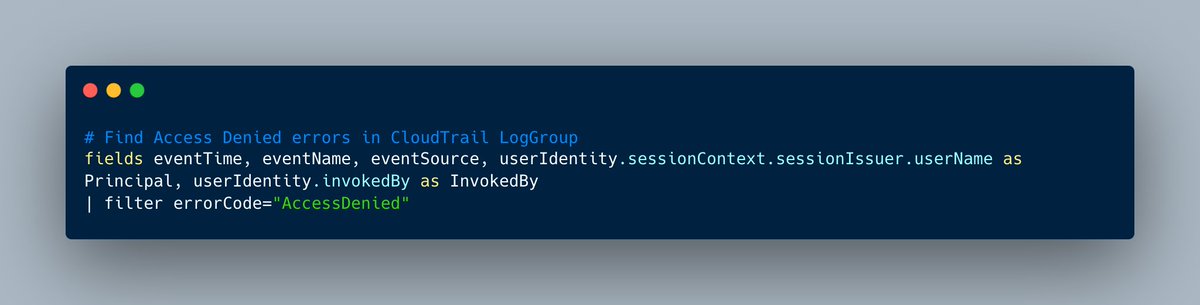
Have you ever wondered what recent AccessDenieds were on your AWS account?
This dead simple CloudWatch Insights query will answer it for you, and you will be surprised.
Copy/PasteOps, see you next tweet 👋
 48
48 4Sep 21 · 5:00 PM
4Sep 21 · 5:00 PM
A lot of cool cloud security research is coming out today! I’m excited to share what we’ve been working on soon :>
 49
49 1Sep 20 · 5:13 PM
1Sep 20 · 5:13 PM- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email









