
Sponsor
There's an IAM change in this Terraform pull request, what do I do?!
You know it, we know it – change is scary, but change is inevitable.
IAM Pulse is bringing much-needed clarity to Terraform change reviews by delivering actionable insights about what could happen downstream if an IAM change is applied.
Join our private beta and get a free AWS IAM Assessment!
In a nutshell
This week, Colm MacCárthaigh (VP / Distinguished Engineer at Amazon Web Services) shared with me his youtube channel.
Folks, it's a pure gold mine. You should definitely check out: Shuffle Sharding
ASD has a new landing-page, if you find this newsletter relevant, please share it with friends :)
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSConfigServiceRolePolicy
- AWSStorageGatewayFullAccess
- AWSStorageGatewayReadOnlyAccess
- AWS_ConfigRole
- AmazonRedshiftServiceLinkedRolePolicy
- AmazonSageMakerCanvasFullAccess
- AmazonWorkSpacesWebServiceRolePolicy









And just like that...with a lot of hard work and gusto I leveled up to L8. From intern to director and all in @AWS. Thank you to everyone on Team Brigid. 📈 🎉🍾

 4.2k
4.2k 111Sep 08 · 1:07 AM
111Sep 08 · 1:07 AM
🧑🎓 Elixir Secure Coding Training
An interactive cybersecurity curriculum designed for enterprise use at software companies using @elixirlang
By @HoldenOullette
github.com/Podium/elixir-…

 192
192 52Sep 06 · 1:00 AM
52Sep 06 · 1:00 AM
✍️ SAML: An Introduction to SAML and its security
Ruxmon 2022 talk by @snyff covering how SAML works and various attacks, including XXE, XML signature shenanigans, malicious identity providers, etc.
#infosec #cybersecurity
docs.google.com/presentation/d…
 163
163 57Sep 07 · 7:00 PM
57Sep 07 · 7:00 PM
New AWS terms and conditions:
- §70.5. AWS wants to avoid responsibility for any use of IQ (I'm surprised that wasn't already there).
- §87🚨 GuardDuty's Malware Protection may copy data outside of the regions you are using it (data governance folks FYI)
diffchecker.com/0C2FtHAU

 67
67 27Sep 06 · 5:25 PM
27Sep 06 · 5:25 PM
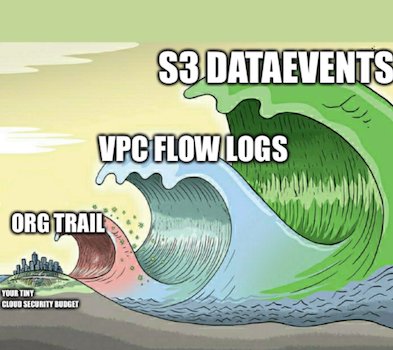
Another crazy good/detailed post about AWS security by @jcfarris
This time it's about incident response chrisfarris.com/post/aws-ir/
The log tsunami vs your security budget picture is my favourite 😄
 58
58 15Sep 06 · 2:04 AM
15Sep 06 · 2:04 AM
Interesting abuse of some github UI and related issues with code exec in the CI pipeline. marcyoung.us/post/zuckerpun…
 55
55 17Sep 11 · 10:07 PM
17Sep 11 · 10:07 PM
If you want to have a real bad time, you should try running a HTTP1/2/3 service on AWS ECS. I've just started day two of this saga and it's not going well. 😰
Has anyone got this working? Issues I've hit in no particular order:
 42
42 7Sep 07 · 2:17 AM
7Sep 07 · 2:17 AM
I’m loving this early period in my startup where we are so focused on building a great product with great people.
I stepped back for a moment last night & realized that this period in my life will always be a special memory.
And we’re just getting started.
Back to the grind 💪🏼
 27
27 0Sep 07 · 6:09 PM
0Sep 07 · 6:09 PMYesterday I said farewell to Turner/WarnerMedia/Discovery. Today I’m on a flight to SouthEast Asia to meet my new team at their first post-pandemic all-hands. Exciting times!

 21
21 0Sep 08 · 5:10 PM
0Sep 08 · 5:10 PMI just wanted to give a shout out to the maintainers of https://github.com/benkehoe/aws-sso-util . It fills in so many little gaps with AWS SSO (which itself may be a bit clunky, but is a service I wish more people made use of). If you're using CloudFormation to manage SSO access …
- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email









