📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:

🔥 Bug Hunter's Methodology: Application Hacking v1
#NahamCon2022 slides by @Jhaddix
* Tech profiling
* Finding CVEs & misconfigs
* Port scanning
* Content discovery
* Spidering
* Analyzing JavaScript & params
+tons of tools for ☝️
#bugbountytips
docs.google.com/presentation/d…
 246
246 74May 11 · 7:00 PM
74May 11 · 7:00 PM
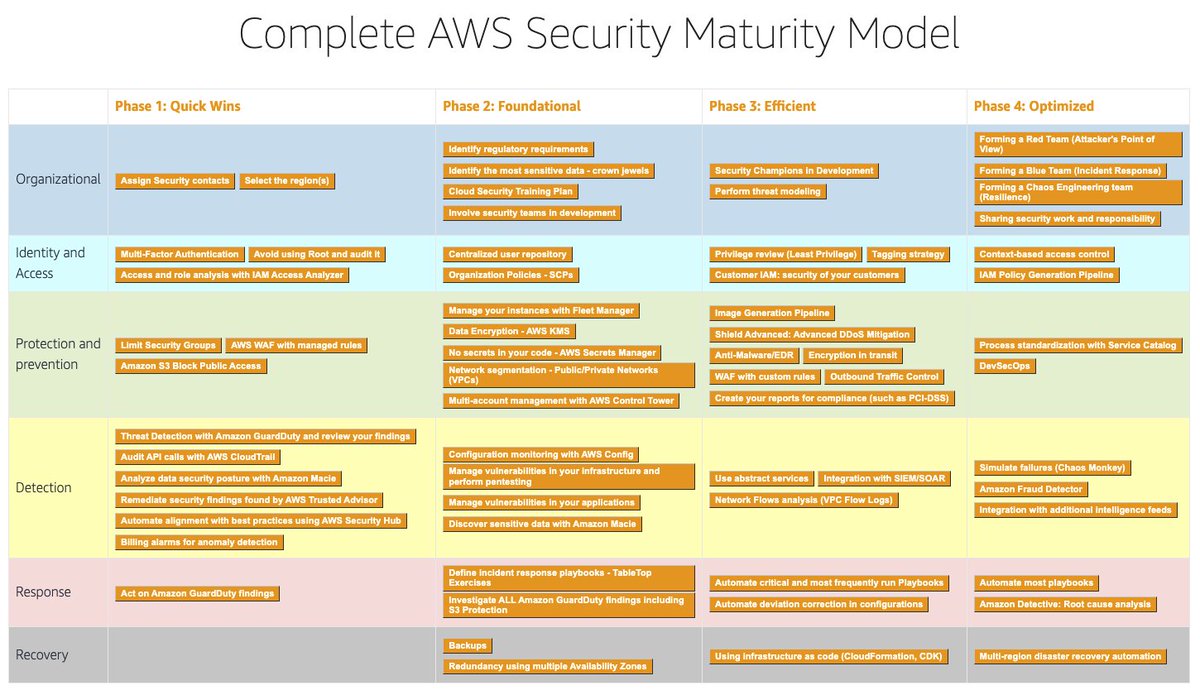
First time I've seen a visual security maturity model from AWS maturitymodel.security.aws.dev/en/model/
The more colours the better! 😁
 240
240 58May 16 · 2:02 AM
58May 16 · 2:02 AM
By my count for Critical Azure incidents in the past 9 months (cross-tenant or unauth RCE) we're at:
🔥🔥🔥 3 Wiz (ChaosDB, OMIGOD, ExtraReplica, +1 High for NotLegit)
🔥🔥 2 Orca (AutoWarp, SynLapse)
🔥1 Palo Alto (Azurescape)

I was able to access #Azure user credentials and run code on other customers’ machines.
The vulnerability is called #SynLapse.
It was a vulnerability in Azure Synapse Analytics (@Azure_Synapse) & Azure Data Factory, exploiting a major flaw in the tenant separation.
(1/3)
 112
112 48May 10 · 3:01 AM
48May 10 · 3:01 AM
📚 tl;dr sec 132
* @Jhaddix Bug Hunter’s Methodology: Application Hacking
* @devec0, @seanyeoh Pwning Cloudflare Pages
* @JackRhysider Why you should be blogging
* @hakluke Bypassing WAFs
* @florenciocano Scanning Dockerfiles with Semgrep
+ more!
tldrsec.com/blog/tldr-sec-…
 99
99 36May 12 · 5:00 PM
36May 12 · 5:00 PM
The tables in this blog post are very powerful for understanding when to use different controls and conditions keys. Awesome work by @IlyaEpshteyn
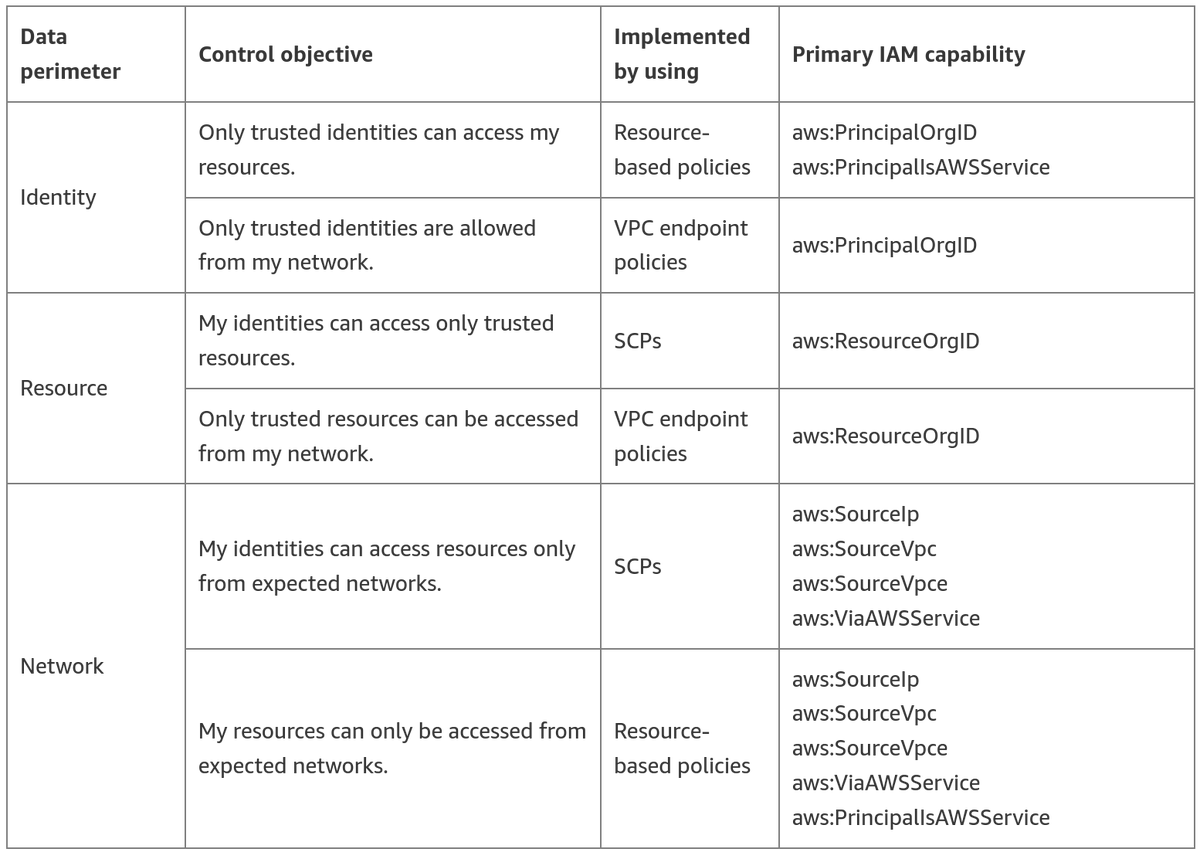

Our new condition keys allow you to limit your principals’ access to include only resources belonging to a specific AWS account, AWS organization, or OU.
Learn how they can form part of a wider security strategy to create a perimeter around your data. 👇 go.aws/3w1KcDi
 93
93 24May 11 · 4:54 AM
24May 11 · 4:54 AM
It's pronounced "Tenets." Like "Tennis" with a final "T." Not "Tenants".
 32
32 4May 13 · 6:30 PM
4May 13 · 6:30 PM
Some exciting changes currently in the RFC phase for CloudFormation. 😍
Ever wanted for-loops in CloudFormation? Now's your chance to have your say! twitter.com/AWSCloudFormer…

Today we launched a new repository that gives you the ability to start, comment, and contribute on #AWS #CloudFormation language improvement discussions. Get started and learn more here: go.aws/3kSWPdt
 27
27 2May 10 · 1:29 AM
2May 10 · 1:29 AM
Pickles went on his first field trip today! It was in the rain and we got wet. But we both loved it!

 15
15 0May 16 · 12:45 AM
0May 16 · 12:45 AM
My friend @anunbhatt wrote a 🔥 blog post outlining a security reference architecture for serverless in AWS. He runs the security reference architecture program at Salesforce. Highly recommend reading this.
Code: github.com/anunay-bhatt/s…
Blog post: anunay-bhatt.medium.com/security-refer…

(1/3) A new article on #serverless security where I use a demo app and demonstrate the integration of security controls - medium.com/p/2fcd25b1d5e2. I hope the #cloudsecurity discussion here will be of help to developers in integrating security early on in their #serverless journey
 9
9 3May 12 · 3:46 AM
3May 12 · 3:46 AMUpdate to the post:
A few users have asked for the code to this project. So here it is. Reminder, nothing is optimized - I'm still learning and haven't gotten to that point yet. And yes, a few items are hardcoded in this version as well. There are a couple …
I am working for a penetration testing company. We have Nessus and Kali installed in AWS. We use them to perform penetration tests against our client targets outside of AWS. We keep getting abuse notices from Amazon, which is hampering our business performance. Is there a way to be a …
hey guys I'm new to this and I'm sorry if its the wrong sub. can you help find papers about UML use cases diagrams saas application's security?
I'm in dev and I'm doing a paper about it.
best example that I have found is outdated : exemple
- 🖊️ This newsletter was forwarded to you? Subscribe here
- 📢 Promote your content with ASD Sponsorship
- 💌 Want to suggest new content: contact me or reply to this email