📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSConfigServiceRolePolicy
- AWSIoTFleetHubFederationAccess
- AWSSecurityHubReadOnlyAccess
- AWS_ConfigRole
- AccessAnalyzerServiceRolePolicy
- AmazonChimeSDKMediaPipelinesServiceLinkedRolePolicy
- AmazonEBSCSIDriverPolicy
- AmazonEventBridgeReadOnlyAccess
- AmazonRDSPerformanceInsightsReadOnly
- AmazonSageMakerServiceCatalogProductsLambdaServiceRolePolicy
[...]

🎉 Docker added a new CLI command to generate a Software Bill of Materials (SBOM) from a Docker image.
`docker sbom` lists system packages *and* language libraries installed. You can use it to get visibility into what packages exist across your infra.
docker.com/blog/announcin…
 305
305 103Apr 10 · 8:42 PM
103Apr 10 · 8:42 PM
eks:CreateCluster

What are the biggest mistakes you see startups making in AWS?
 282
282 31Apr 05 · 5:15 AM
31Apr 05 · 5:15 AM
🔥 Trufflehog v3 🔥
🏎️ Faster: rewritten in Go
🔬 Detects >600 credential types
✅ Actively verifies if creds still work => no FPs
☁️ Native support for scanning GitHub, GitLab, filesystems, and S3
#bugbounty #bugbountytips
github.com/trufflesecurit…

We're so happy to Open Source TruffleHog V3! youtu.be/AM3REzw1LDk
 117
117 49Apr 05 · 10:57 PM
49Apr 05 · 10:57 PM
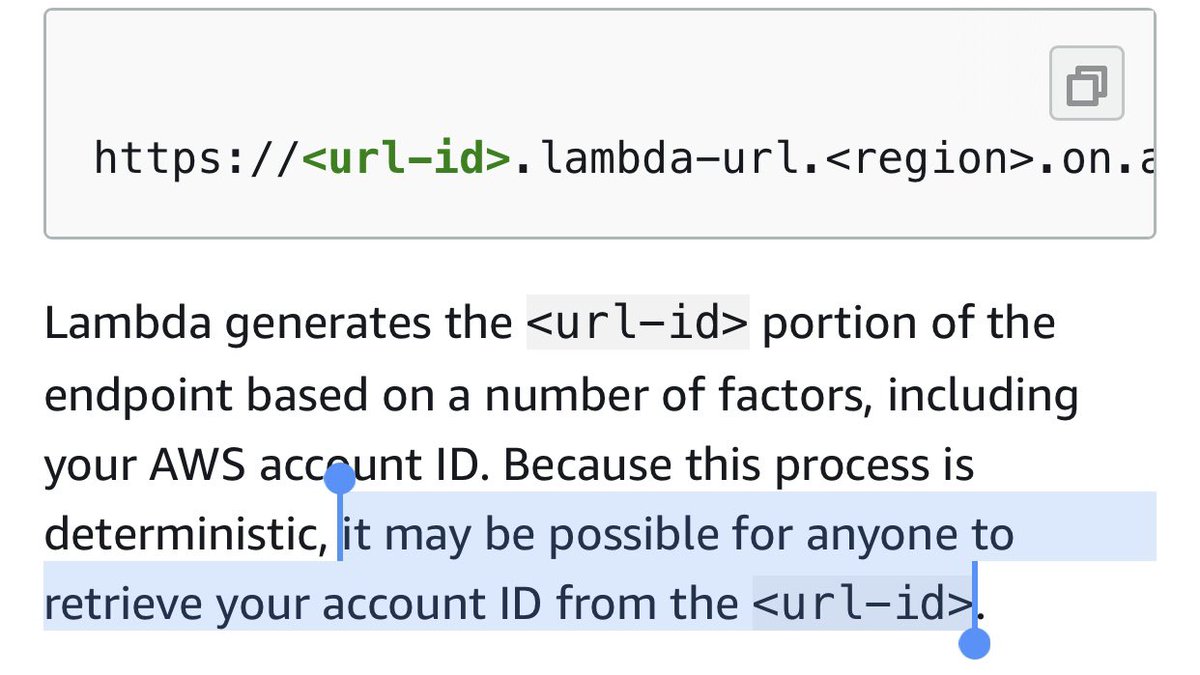
Has anyone figured out the deterministic process described in the Lambda function URL docs?
It feels like they put this highlighted part here solely to tempt me into wasting time figuring it out. And I’ve completely fallen for it.
 99
99 14Apr 07 · 10:33 AM
14Apr 07 · 10:33 AM
Since lambda malware is getting recent attention, this talk is perhaps the earliest talk around lambda malware (2016), and is very entertaining: youtube.com/watch?v=YZ058h…
 61
61 13Apr 07 · 8:46 PM
13Apr 07 · 8:46 PM
What if AWS starts to apply extra costs to insecure resources? Like applying extra fees to public S3 buckets, IAM Users with unused AK/SK or without MFA, Unauthentified APIGW, etc...?
They are already applying extra costs to orphaned EIPs. Same things but for security.
 55
55 9Apr 08 · 3:13 PM
9Apr 08 · 3:13 PM
Great post on Security Engineering, scaling security, encouraging devs to proactively up security posture, dashboards, and more.
CC people who will probably enjoy: @frgx @DanielMiessler @manicode @travismcpeak @coffeetocode @nicowaisman @shehackspurple @ejcx_ @laraghavan

🆕 Just wrote this article about what I've been building at work 🥳 We're hiring!
Monocle: How Chime creates a proactive security & engineering culture (Part 1)
medium.com/life-at-chime/…
 41
41 13Apr 08 · 1:07 AM
13Apr 08 · 1:07 AM
Looks like how AWS evaluates IAM permissions once you add in boundaries, SCPs, conditions, resource policies, I could go on.

Isn't that the BGP path selection algorithm?

 45
45 4Apr 09 · 3:33 AM
4Apr 09 · 3:33 AM
I don't think GuardDuty can detect lambda miners (maybe GD experts like @123Le_Bron can correct me), because GD has 3 source of input:
1. CloudTrail: This miner doesn't make AWS calls
2. DNS: This uses DNS over HTTP
3. VPC Flow Logs: I'm unsure if this would detect it. 🧵

This is some fun analysis of (the first?) malware designed to run in AWS Lambda by @_mattmuir >
cadosecurity.com/cado-discovers…
 40
40 5Apr 07 · 5:33 PM
5Apr 07 · 5:33 PM
I was informed by a friend that Cognito seems to have updated their processing rules for Hosted UI CSS configurations.
The previous "do what you want" rules no longer apply and there's now a filter on upload, but can we bypass this to add a nice background? Let's find out 🕵️ 1/

Have you ever used Cognito's Hosted UI and found it very limiting in its customization options? (drop shadows and plain backgrounds🤢)
Well today I've figured out a way to fully customize the CSS, so you can make beautiful looking pages like this: 😍
…auth.ap-southeast-2.amazoncognito.com/login?client_i…
1/

 31
31 2Apr 08 · 4:58 AM
2Apr 08 · 4:58 AMI created an S3 bucket then went to upload some test/junk python scripts like...
$ aws s3 cp --recursive src s3://${BUCKET}/abc/code/
It worked! Then I realized that the ${BUCKET} env var wasn't set, huh? It turns out I uploaded to this mysterious s3://abc/ bucket. Writing and listing the the contents …
We experienced a significant uptick in charged from something done on January 31st that I am currently unable to explain.
TimedStorage-ByteHrs (GB-Month) jumped up between 1/31/22 into 2/1/22 across multiple accounts, every bucket, and every storage class that I have no idea how to explain. The screenshot below is a …
If a dev has found a vulnerability on his system. How should a cloud security engineer help research this vulnerability and help implement a fix if there is one.
- 🖊️ This newsletter was forwarded to you? Subscribe here
- 📢 Promote your content with ASD Sponsorship
- 💌 Want to suggest new content: contact me or reply to this email







