I'm opening sponsorship on AWS Security Digest. Please contact me, if you want to promote AWS Security related content.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:

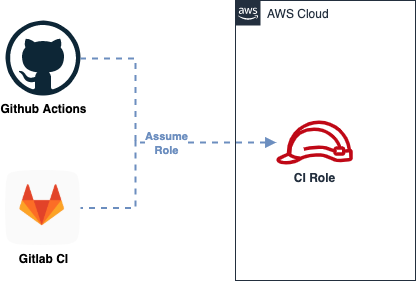
I've just open sourced a small Terraform module which automates the setup of OIDC federation between AWS and Github Actions/Gitlab CI:
github.com/marco-lancini/…

I'm just going to put this out there: gatekeeping is one of the worst traits in humans, and if it's the only way you can make yourself feel good you should rethink your life.

No AWS SDK updates yesterday or today reminds me that it is annual performance review week at AWS.

Reminder to vendors: If your product deploys EC2s in customer environments without IMDSv2, I am going to be putting you on a public shame list. This includes AWS's own features such as their new EC2 fast launch that doesn't work if you enforce IMDSv2.

AWS Announces New Launch Speed Optimizations for Microsoft Windows Server Instances on Amazon EC2
Today AWS announced the ability to launch Microsoft Windows Server instances up to 65% faster on Amazon Elastic Compute Cloud (EC2). Customers can fla... aws.amazon.com/about-aws/what…

When I was in security consulting, I was telling management about scanning Terraform, securing CI/CD, golden images, overprivileged roles, etc. They didn’t think those were important and were stuck in the past.
5 years later, it’s now standard architecture. I feel vindicated.

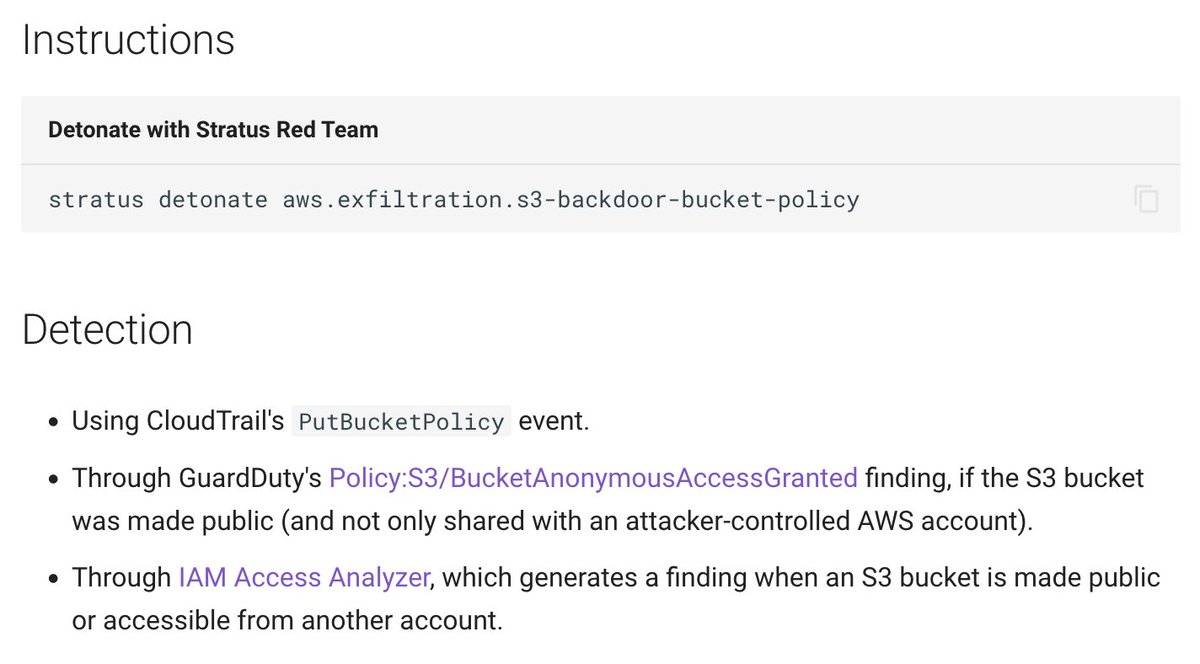
Stratus Red Team v1.2.0 adds:
• Documentation for detecting common attack techniques using CloudTrail, GuardDuty, Access Analyzer
• 2 new attack techniques (discovery & exploitation of EC2 user data)
👉 github.com/DataDog/stratu…
📈 Next up: Support for common Kubernetes TTPs!

📢 Today, I'm thrilled to announce "Stratus Red Team", an open-source adversary emulation tool for the cloud!
Comes with a catalog of cloud-native attack techniques that you can easily detonate to test your threat detection.
github.com/Datadog/stratu…
📝blog.christophetd.fr/introducing-st…


I’m seeing this article get circled round, and it’s not incorrect, but the only advice regarding AWS IAM users that matters is that you should purge the bloody things from your environment wherever possible. Set up an SSO and use roles for everything.
iampulse.com/articles/aws-i…

You asked, so I'll deliver. This is what I know about responsible disclosure/#CVD/how to report security issues in other people’s software. Call it "10 Commandments of Durson" if you want. 🧵
I was going to allow certain users to upload relatively small videos of 50mb or less.
I've heard an s3 bucket isn't good for serving videos. Is this mostly because of the costs? Or speed? Or other reasons?
For 50mb videos would an s3 bucket serving video still be problematic? …
I have problem with corrupted system table in Aurora. I have searched everywhere and the only solution seems to be "write AWS support ticket and they will fix it". I have developer support which costs me $350/month, so I created support ticket (9520368991) but it is still "unassigned" after 10 …
I would like to be able to pass a starting point to a tool, say an EC2 for example, and then it builds a list of dependencies, like any Security Groups, policies, ALB’s that use it, etc. Either as a diagram or at least as a list or something useful. …
My question is is there a way/tool I could fetch log events from all these solutions and aggregate in a single account and therefore have a single point of truth as well as some visibility for security?
- 🖊️ This newsletter was forwarded to you? Subscribe here
- 📢 Promote your content with Sponsorship
- 💌 Want to suggest new content: contact me or reply to this email