🔦 Highlight of the week
- Orca Security Research Team Discovers AWS CloudFormation & Glue Vulnerabilities
- 2021 AWS security-focused workshops
- Implementing a Vulnerable AWS DevOps Environment as a CloudGoat Scenario
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSAppRunnerFullAccess
- AWSBackupServiceLinkedRolePolicyForBackup
- AWSPanoramaFullAccess
- AWSServiceRoleForAmazonEKSNodegroup
- AWSWAFConsoleFullAccess
- AWSWAFFullAccess
- AppRunnerNetworkingServiceRolePolicy
- LightsailExportAccess
Get notified of policy change using this Twitter bot. 🐦
🆕 MASE - Monitor AWS Services and Regional Endpoints on Twitter
Initial Publication Date: 2022/01/13 13:00 PST
Security researchers recently identified and reported an issue in AWS CloudFormation. Specifically, the reported issue was in the AWS CloudFormation service itself, which allowed viewing of some local configuration files on an AWS-internal host or attempted unauthenticated HTTP GET requests from the same host. …
Initial Publication Date: 2022/01/13 13:00 PST
A security researcher recently reported an issue that allowed them to take actions as the AWS Glue service. Utilizing an AWS Glue feature, researchers obtained credentials specific to the service itself, and an AWS-internal misconfiguration permitted the researchers to use these credentials as the …







😱😱😱 This is worse than ChaosDB for AWS. @orcasec gained access to all AWS resources in all AWS accounts! They accessed the AWS internal CloudFormation service.
orca.security/resources/blog…
Separately, they did something similar for Glue.
orca.security/resources/blog…


Wanted to share two items that are now public. Thank to @orcasec for their collaboration with us at AWS's security team on this research into Glue and CloudFormation each technique was mitigated within days of their reports and there was no customer impact. 🧵

Amazon SNS now supports ABAC! 🙌 aws.amazon.com/about-aws/what…. For more on the basics & benefits of ABAC in AWS: aws.amazon.com/identity/attri…

AWS has published security bulletins for this:
- aws.amazon.com/security/secur…
- aws.amazon.com/security/secur…
This is a new direction for AWS to not only publish a bulletin for something like this, but also to thank Orca publicly. 👏

(1/13) People seemed to like the thread last week about silly IPv6 TOTP possible in AWS EC2. But then @donkersgood said I should do something useful instead.
So here are some useful things that are possible thanks to the AWS Gateway Load Balancer

What's the silliest use for 281 trillion IP addresses?
I made a thing that uses the new-ish AWS EC2 support for assigning IPv6 prefixes to EC2 instances. You can only connect to the instance when the IP ends in a TOTP 6 digit authenticator code. How/why:
github.com/aidansteele/ip…

We have a new CloudGoat scenario, contributed by @christophetd from @datadoghq!
Check it out: github.com/RhinoSecurityL…

🔥🔥 love attacking CI/CD pipelines. They’re basically RCE as a service by design - ripe for abuse. To secure it you have to really think like an attacker.
Thanks NCC group for sharing these war stories. Love it

🤔 10 real-world stories of how we’ve compromised CI/CD pipelines research.nccgroup.com/2022/01/13/10-… #infosec

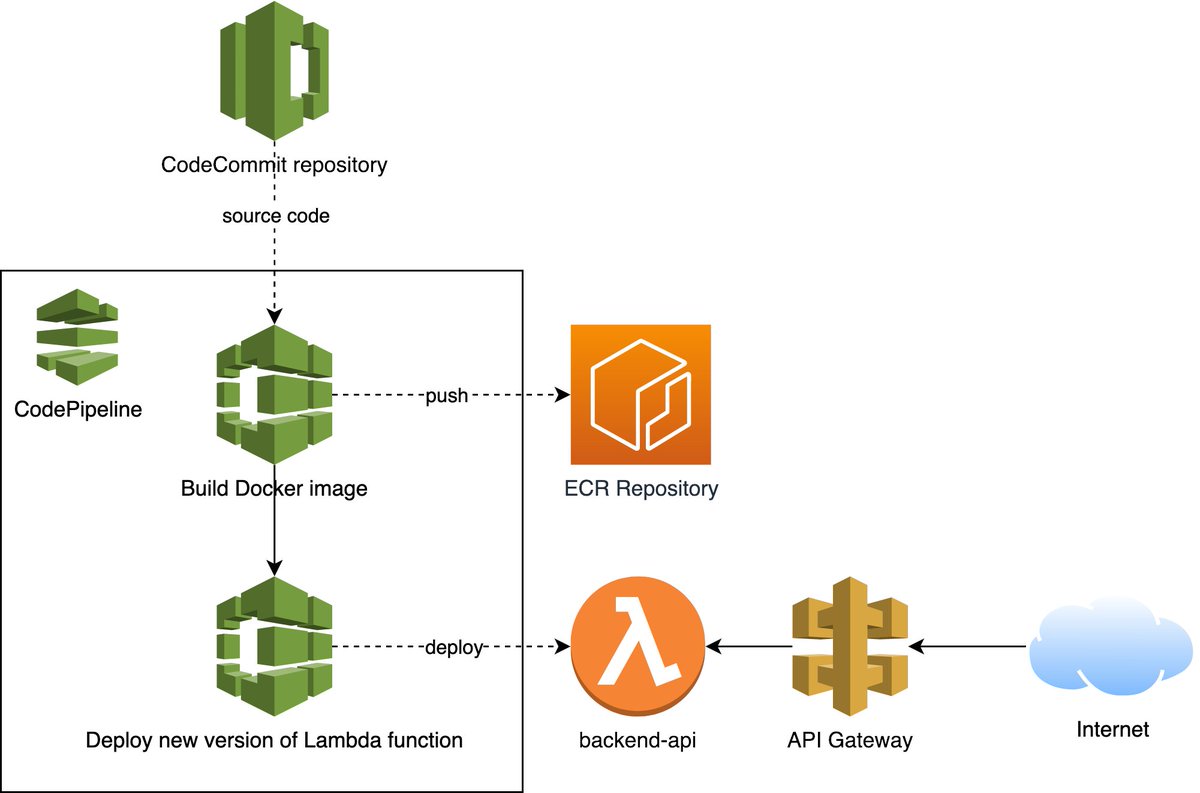
I contributed to a new CloudGoat scenario: a vulnerable "modern AWS DevOps environment" with an API, simulated user activity, and a continuous deployment pipeline
Making-of: blog.christophetd.fr/implementing-a…
Bonus: Writing end-to-end tests for Terraform-based security labs with Terratest

We have a new CloudGoat scenario, contributed by @christophetd from @datadoghq!
Check it out: github.com/RhinoSecurityL…

🛡️ Advocate: Prevent SSRF in your Python apps
Advocate is a drop-in replacement for `requests` that makes it easy to safely make HTTP requests on behalf of a third party
* Deny internal IPs or specific hosts/domains
* Handles DNS rebinding & redirects
pypi.org/project/advoca…
Hello AWS humans, I'd like to congratulate you on the new Console Home - I'm impressed. I honestly like what I see, and didn't think you had it in you to make such thing. Congrats! And keep it coming 🥳
I've been doing developer for 11 years now. I've primarily used GitHub, Gerrit, Gitlab, and now CodeCommit. I cannot believe how barebones CodeCommit is. Describing it as batteries not included doesn't even begin to explain the feature gap between it and something like Gitlab. I really feels like AWS is …
Disclaimer: It's not entirely AWS' fault. Kubernetes is notoriously fickle about versioning between its APIs and addons. Telemetry and infrastructure teams also aren't always the easiest to get on the same page in terms of creating a seamless "product". Plus, stuff that's leveraged by Container Insights mixes a variety of …
hi guys! i’m a student of a west african university & currently in my final year but in order to complete my degree programme in computer science, i would have to write a project (a well written and gratifying one)
you’re my family, my tech family. i request that you …
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew
- 🐦 Follow me on Twitter or hire me.