🔦 Highlight of the week
- PolicyGlass is a Python Package that allows you to analyse one or more AWS IAM policies' effective permissions in aggregate
- Don't Make My Mistakes: Common Infrastructure Errors I've Made
- Amazon GuardDuty has updated the following finding types to help identify and prioritize issues related to CVE-2021-44228 and CVE-2021-45046
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AmazonFISServiceRolePolicy
- AmazonLookoutMetricsReadOnlyAccess
- AmazonMSKFullAccess
- FMSServiceRolePolicy
Get notified of policy change using this Twitter bot. 🐦
🆕 MASE - Monitor AWS Services and Regional Endpoints on Twitter

What's the silliest use for 281 trillion IP addresses?
I made a thing that uses the new-ish AWS EC2 support for assigning IPv6 prefixes to EC2 instances. You can only connect to the instance when the IP ends in a TOTP 6 digit authenticator code. How/why:
github.com/aidansteele/ip…

Imagine how much worse this could have been (and how long it would have gone undetected) if the change was siphoning AWS credentials instead of graffiti in the terminal.

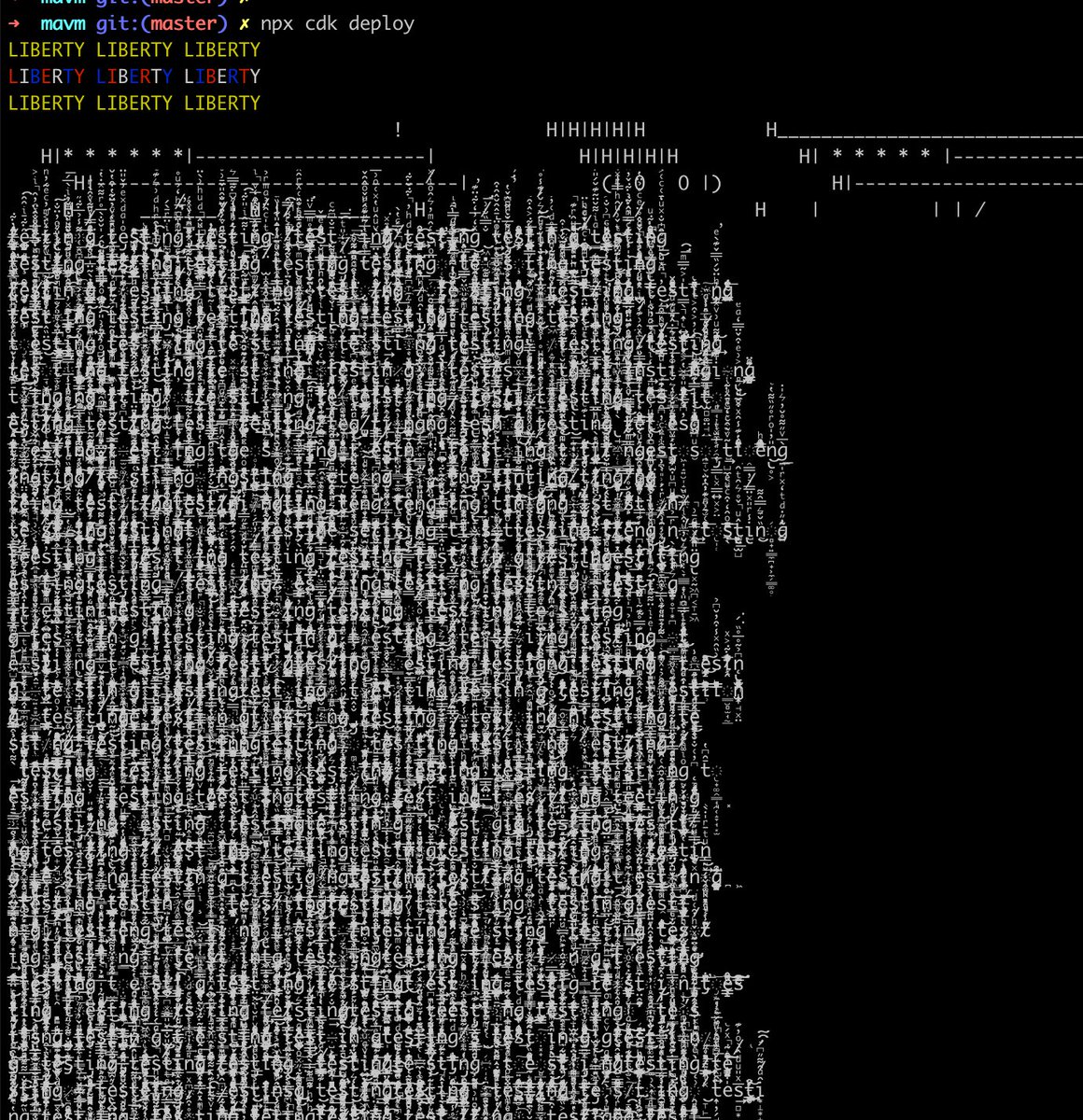
Looks like the AWS CDK is broken because the dependency on colors.js which has a totally hilarious bug: github.com/aws/aws-cdk/is…
It shows "LIBERTY LIBERTY LIBERTY".

🔭 Web Cache Vulnerability Scanner
A Go-based CLI tool for testing for web cache poisoning by @m10x_de
Supports 9 different web cache poisoning techniques
#bugbountytips #Pentesting
github.com/Hackmanit/Web-…

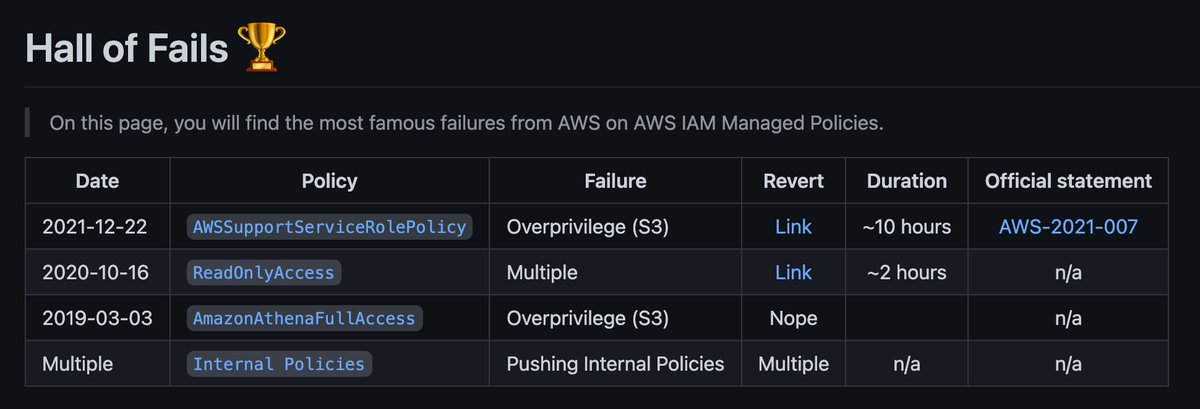
I've started to reference all mistakes made by AWS on IAM AWS Managed Policies on this "Hall of Fails" markdown file.
Feel free to issue PR and add your contribution. 👌🏼 github.com/z0ph/MAMIP/blo…

Time to retire the bastions that use port knocking. The new trick is shuffling the IPv6 address based on a TOTP code. 😂 Finally TOTP support for any protocol.

What's the silliest use for 281 trillion IP addresses?
I made a thing that uses the new-ish AWS EC2 support for assigning IPv6 prefixes to EC2 instances. You can only connect to the instance when the IP ends in a TOTP 6 digit authenticator code. How/why:
github.com/aidansteele/ip…

Got tired of all those Reddit posts about hacked #AWS accounts and decided to write this guide for setting up an account and staying within the free tier. This one is a bit more oriented towards beginners, but hopefully useful! #CloudComputing
matthewdf10.medium.com/so-you-want-to…

"There is still SO MUCH CSRF to find in bounty programs." -@hakluke
His 🧵 with tips on how:
twitter.com/hakluke/status…
🛠️ XSRFProbe by @0xInfection
A CSRF audit and exploitation toolkit that can crawl sites and generate PoCs when a vuln is found
github.com/0xInfection/XS…

There is still SO MUCH CSRF to find in bounty programs.
CSRF comes in many forms. Try:
- Removing the token parameter entirely
- Setting the token to a blank string
- Changing the token to an invalid token of the same format
- Using a different user's token
More in thread 👇

This is an interesting change. You shouldn't have anything sensitive on your tags, and if an attacker can access the metadata service you're having a bad day anyway.

Instance Tags now available on the Amazon EC2 Instance Metadata Service
You can now access your instance's tags from the EC2 Instance Metadata Service. Tags enable you to categorize your AWS resources in different ways, for example, by purpose, own... aws.amazon.com/about-aws/what…
Just wanted to post a thank-you for all the hard lessons learned by the community.
It was the final motivation I needed to setup MFA across all of my environments in all of my projects.
I've been delaying the setup for months. Thanks for the motivation!
Hopefully this serves as …
My take on the recent "December" outages. I have seen too many articles talking about Multi-Cloud in the past month, while there is a lot that can be done in terms of disaster recovery before even considering Multi-cloud.
Our S3 storage was a bit unoptimized and with bucket analytics and lifecycle rules, we've managed to reduce the costs from $3400/month to $300/month.
The last piece of the puzzle was to switch from Standard IA to Glacier Instant Retrieval which enabled an additional reduction of 60% on top of …
TLDR;: Forget to check the hidden "Delete on Termination" checkbox for the EBS volumes of your Launch Config that is attached to the ASG of the capacity provider of your ECS cluster. Good times.
A couple of months ago, we had some performance issues and determined it was best to …
Example : What is the difference between endpoint security of a win10 laptop vs win10 VM on a cloud ?
We are essentially deploying the same AV solution on both of them, so what is the difference ?
Any reading material, link etc would be appreciated.
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew
- 🐦 Follow me on Twitter or hire me.












