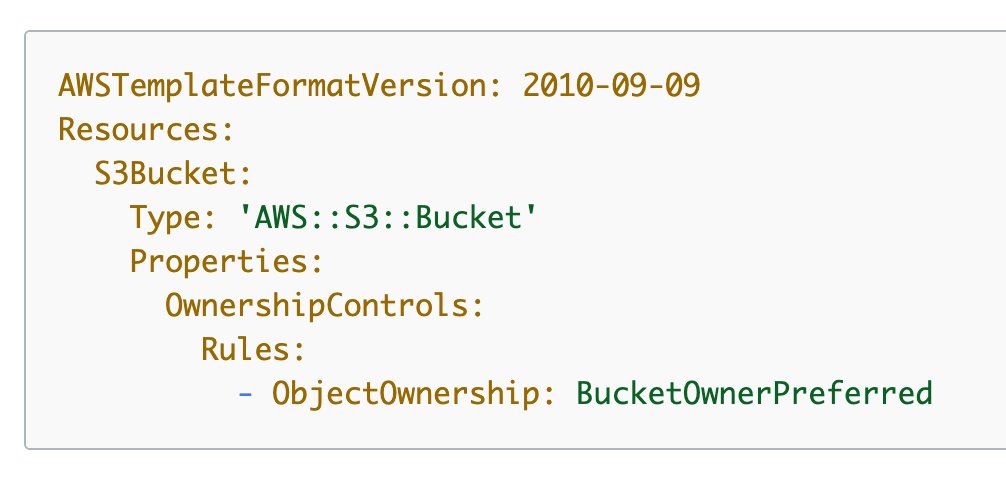
Amazon Macie announces a slew of new capabilities including support for cross-account sensitive data discovery, scanning by Amazon S3 object prefix, improved pre-scan cost estimation, and added location detail in findings
We are excited to announce a series of new capabilities that have been added to Amazon Macie to make it easier to configure, scope, and run sensitive data discovery in AWS, including support for scanning jobs that cover Amazon S3 buckets residing across multiple accounts, scoping of scans by object …