🔦 Highlight of the week
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSDataExchangeFullAccess
- AWSDataExchangeProviderFullAccess
- AWSIPAMServiceRolePolicy
- AWSMarketplaceSellerFullAccess
- AdministratorAccess-Amplify
- AmazonEMRContainersServiceRolePolicy
- AmazonMSKFullAccess
- AmazonSageMakerReadOnly
- AmazonWorkSpacesWebReadOnly
- AmazonWorkSpacesWebServiceRolePolicy
Get notified of policy change using this Twitter bot. 🐦





I've begun a list of security mistakes made by Cloud Service Providers (AWS, GCP, Azure). Includes CVEs, SOC 2 Type 2 failures, security researchers compromising managed services, and more.
github.com/SummitRoute/cs…

As the #reinvent is ending and the #replay hungover is starting, let me re:Introduce this 2021 one-pager recap of all #AWS announcements:
github.com/zoph-io/awscon…

Security folks, pay attention to this one. This is one of those sneaky-powerful re:Invent releases that you might miss. Disable S3 ACLs (which predate AWS IAM's 2010 release) so that all access control is through IAM policies. @AWSIdentity

Amazon S3 Object Ownership can now disable access control lists to simplify access management for data in S3
Amazon S3 introduces a new S3 Object Ownership setting, Bucket owner enforced, that disables access control lists (ACLs), simplifying acces... aws.amazon.com/about-aws/what…

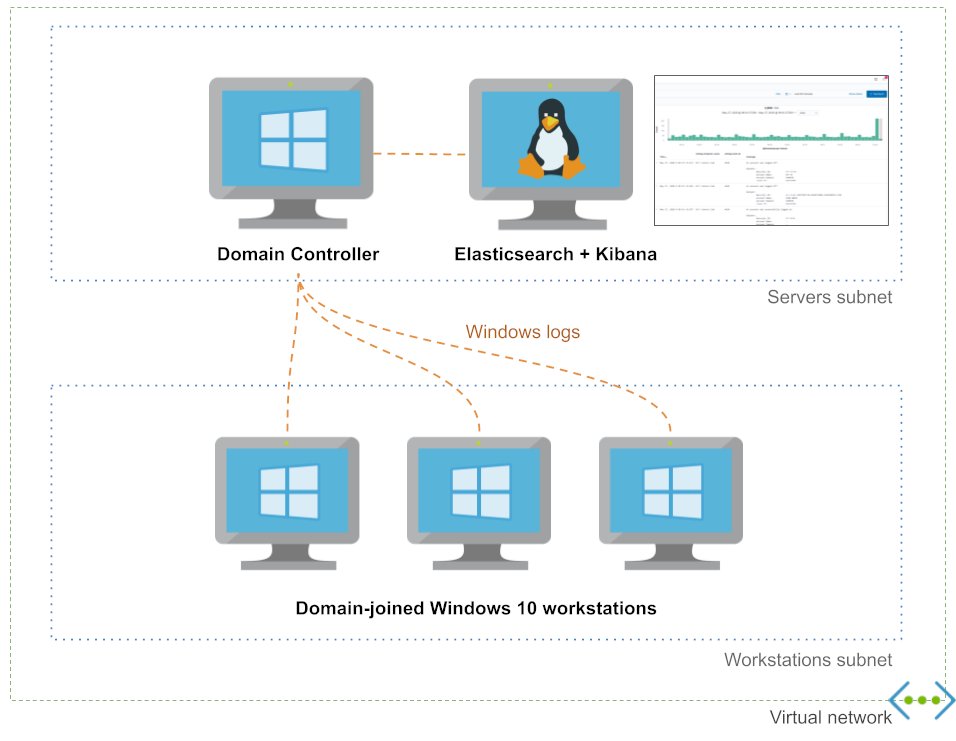
More than a year ago, I started building Adaz - a project to easily spin up disposable AD hunting labs in Azure with 1 DC and X workstations, pre-configured with Sysmon and ELK.
github.com/christophetd/A…
I'm considering whether it's worth investing time in improving it... (1/2)

I started my new job as Staff Security Engineer at @Square today 😃 I couldn’t be more excited to be working with a rockstar team of cloud security engineers at such an amazing company.

This is the highlight of reinvent for me. It’s done, can’t get better than this

Ephemeral storage coming to Lambda! Up to 10Gb! Pre-announced at #reInvent #serverless


🐋 Learning Containers From The Bottom Up
@iximiuz recommends:
1. Linux Containers - low-level impl details
2. Container Images - what images are and why you need them
3. Container Managers - how Docker helps containers coexist
4. Container Orchestrators
iximiuz.com/en/posts/conta…

This attack uses the gamut of webapp exploit techniques applied to AWS. If an attacker knew the name of your SageMaker notebook, and convinced you to click a link, they could get RCE inside the notebook.

Harden your AWS environment is important because you can never know how an attacker can break in 😈
and here is our example:
Cross-Account Access vulnerability in AWS SageMaker Jupyter Notebook Instance
blog.lightspin.io/aws-sagemaker-…

🚀Excited to announce the new Amazon Inspector has been re-architected to deploy in a few clicks, automatically discovering both EC2 & ECR workloads, continually scanning them for software vulnerabilities. More during my Thurs leadership session go.aws/3o2lFK1🚀#reInvent

The real #reInvent life. Taking a call from the hallway floor.

Take a drink every time you hear "Digital transformation". I'll see you in the ER when we all get alcohol poisoning!
Usually every year I hear price cuts, really big features, and etc for developers, but it seems like this year things were just much smaller overall. I hope this isn't a trend year to year.
I was expecting to hear about aurora serverless v2, AWS AppRunner new features, extra serverless …
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew
- 🐦 Follow me on Twitter or hire me.









