📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSBackupServiceLinkedRolePolicyForBackup
- AWSMigrationHubStrategyCollector
- AWSMigrationHubStrategyConsoleFullAccess
- AWSMigrationHubStrategyServiceRolePolicy
- AWSPanoramaApplianceServiceRolePolicy
- AWSPanoramaFullAccess
- AWSPanoramaServiceLinkedRolePolicy
- AmazonChimeSDK
Get notified of policy change using this Twitter bot. 🐦

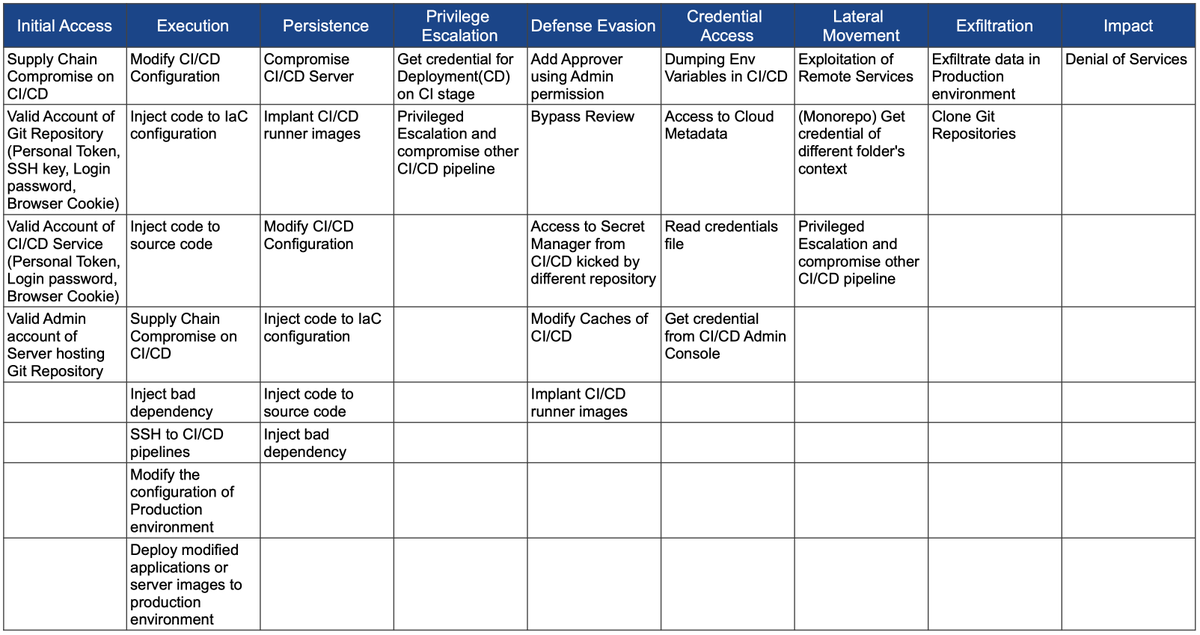
🛡️ Attacking and Securing CI/CD Pipelines
@rung's talk covers why CI/CD pipeline security is important, relevant breaches, several attack scenarios, and how to defend
ATT&CK-like matrix for CI/CD Pipelines. Repo 👇
github.com/rung/threat-ma…
speakerdeck.com/rung/cd-pipeli…
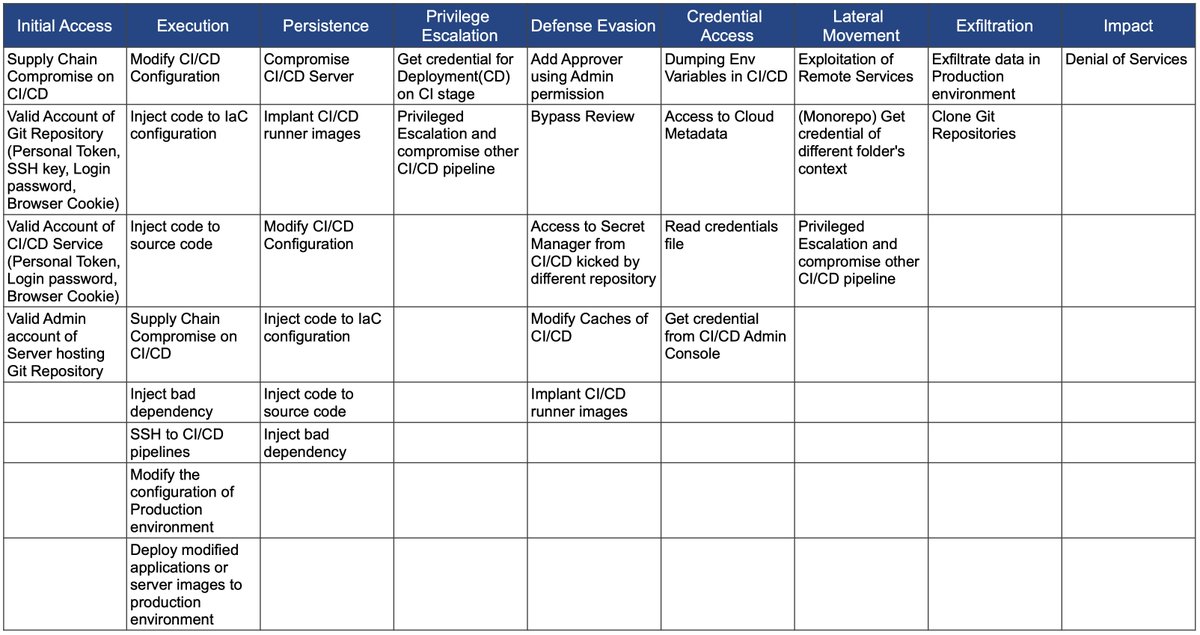

TTPs for compromising CI/CD pipelines, by @rung
github.com/rung/threat-ma…

🗡️ Awesome Linux #Rootkits
Repo with links to source code of 10s of Linux rootkits
Both user mode and kernel mode
github.com/milabs/awesome…

AWS execs need to read this to see how users of other cloud providers don't have to deal with the limitations AWS has.

Example of security and (micro-)economics needing to be aligned.
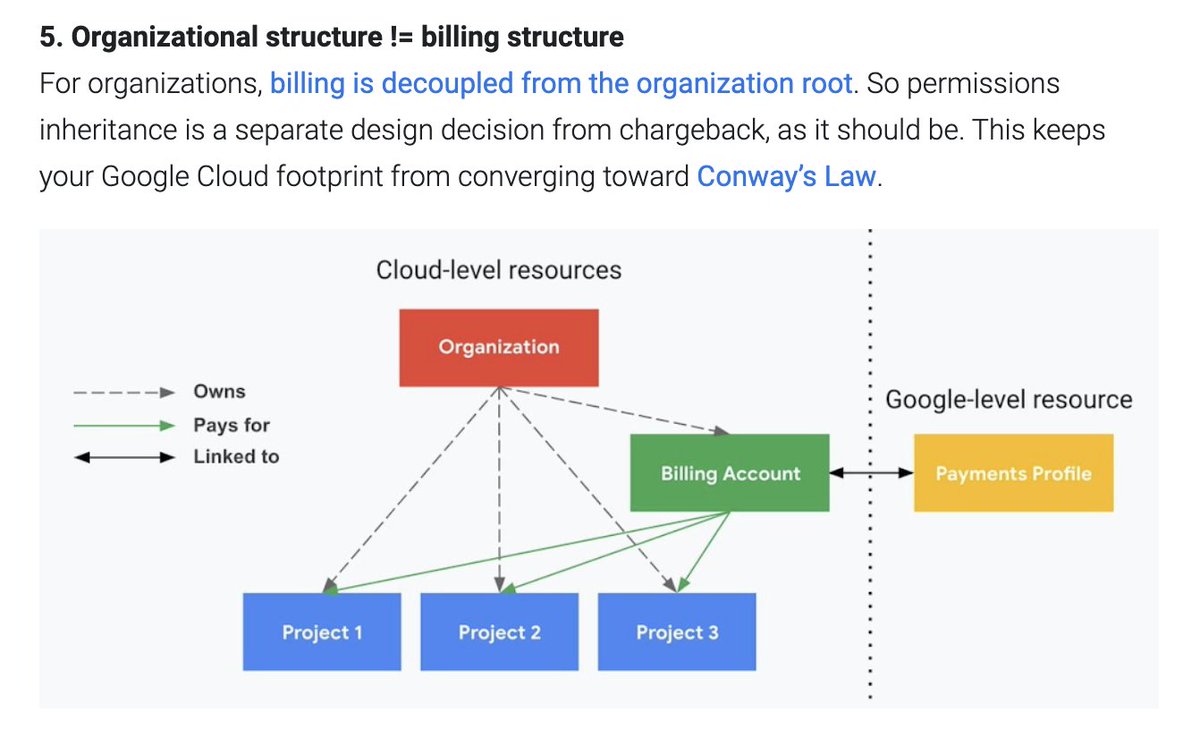
This is a great post from @forrestbrazeal esp. the crucial point on org/project structure decoupling from billing is crucial.
Billing "boundaries" are not usually security boundaries.
cloud.google.com/blog/products/…

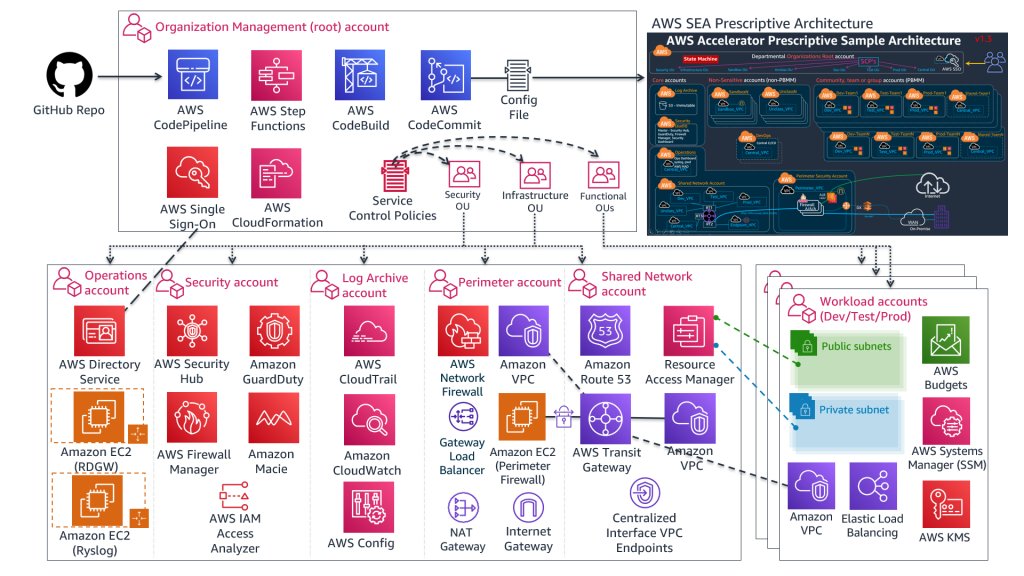
A new major release of AWS Secure Environment Accelerator (ASEA) is out (1.5), check out as there are some interesting new features, like the possibility to install it on top of AWS Control Tower.
- github.com/aws-samples/aw…

The entire training is under 700 words. learnsecurity.amazon.com/training/story…

Starting today, we're making the same cybersecurity training used by Amazon employees available to businesses and individuals around the world at no cost. #CybersecurityAwarenessMonth aboutamazon.com/news/community…

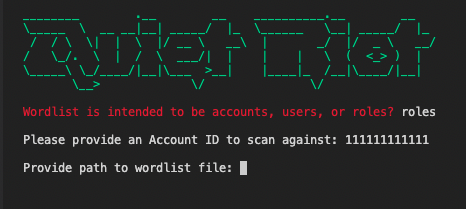
🔥@WesLadd dropped a new AWS security tool, Quiet Riot - unauthenticated enumeration and footprinting of AWS accounts that can validate AWS Account IDs and services in use (via existing service linked role names) at a rate of 1100 requests per second.
blog.traingrc.com/introducing-qu…

Me: Asks a very, very specific question in an online forum related to cloud security
**immediately receives 3 DMs from friends asking me what the hell I am up to**
😈

Reinvent presentations are like gas. To create them, they will take up as much time as you give them.
I was billed 60k having only signed up for the free tier, what is this? Contacted aws support and they told me this was correct and that all usage above the free tier was billed like normal. My site has not seen activity that indicates that this is correct? What …
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew
- 🐦 Follow me on Twitter or hire me.










