
🔥New blog post🔥
"#AWS privilege escalation: exploring odd features of the Trust Policy"
a.k.a.
how to assume an IAM role without "sts:AssumeRole" permission?
rzepsky.medium.com/aws-privilege-…

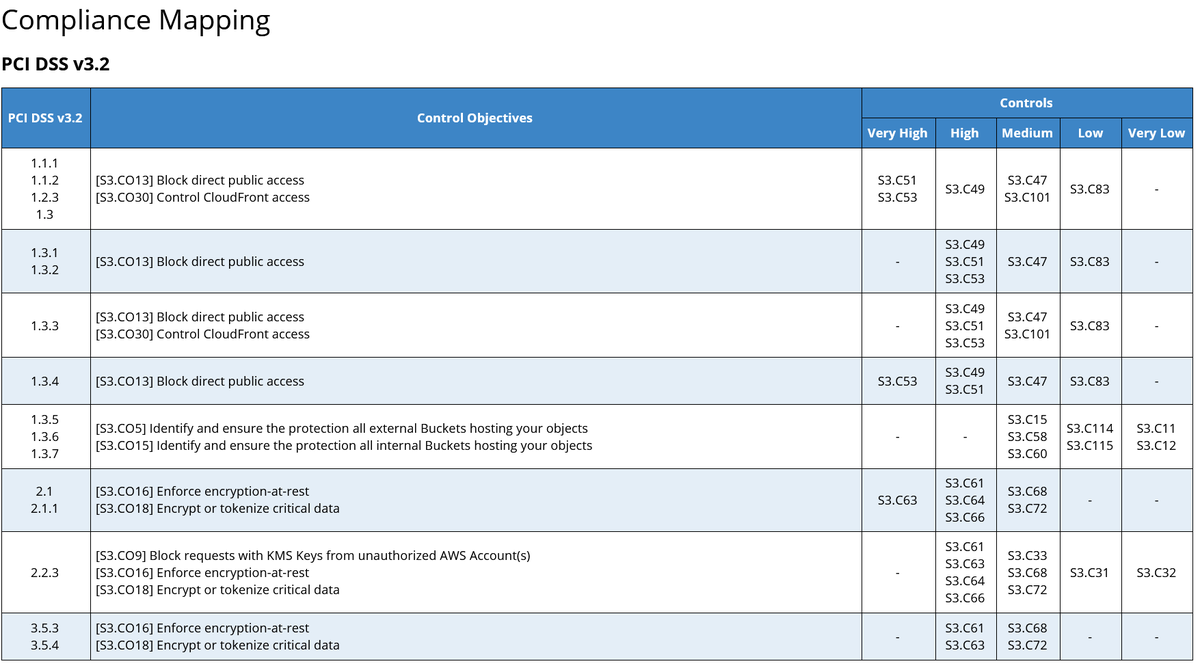
📓 163 page Threat Model of #AWS S3 by @djo_hk
Covers:
1. Best practices (best security/effort ratio)
2. Onboarding for large enterprises/agencies
3. Compliance mapping to demonstrate a risk-based approach and gap analysis
#cloudsecurity
trustoncloud.com/the-last-s3-se…

Access Denied errors are going to say why type of policy is denying them! (SCP vs resource vs IAM vs boundary vs VPC end-point, etc.) This is going to be a huge help for debugging these.

The AWS Security, Identity & Compliance Blog #AWSSecurity
aws.amazon.com/blogs/security…
By: Guaravee Gandhi*

🔥🔥 Crazy exploit on Azure Cosmos DB. “In short, the [Jupyter] notebook container allowed for a privilege escalation into other customer notebooks… As a result, an attacker could gain access to customers’ Cosmos DB primary keys… and the notebook storage access token.”

I'm excited to share information about our research, in which we (+@nirohfeld) found a critical vulnerability in Azure Cosmos DB itself - effectively allowing malicious actors to fully compromise databases of thousands of customers. @wiz_io #ChaosDB chaosdb.wiz.io

⚛️ Electron Hardener by @1Password
A @rustlang library and CLI tool to harden @electronjs binaries against runtime behavior modifications
github.com/1Password/elec…

Numerous cloud vendors ask for "ReadOnly" access via a managed policy. You should think long and hard about what you're actually giving them.
#AWS #cloud #security
posts.specterops.io/aws-readonlyac…

There is now an EC2 IMDS end-point for IPv6 so there will be a new place to acquire creds beyond 169.254.169.254 at fd00:ec2::254. github.com/aws/aws-sdk-go…
The SDK started supporting it a few weeks, but looks like now EC2 has it.
github.com/aws/aws-sdk-go…

😊Had a blast talking about AWS permissions at #reInforce with Karen and Jesse! Least privilege is one of my favorite thing to talk about. 🥳


Coming in October: We are making it easier to protect sensitive data by offering free MFA devices to AWS account holders and Security Awareness Training. More details aws.amazon.com/blogs/security…

This is the holy grail for cloud adversaries: crossing the customer isolation boundaries of the service provider to access other customers' data.
#azure #cloud #security

I'm excited to share information about our research, in which we (+@nirohfeld) found a critical vulnerability in Azure Cosmos DB itself - effectively allowing malicious actors to fully compromise databases of thousands of customers. @wiz_io #ChaosDB chaosdb.wiz.io
https://preview.redd.it/pd30dsv9kbk71.png?width=1906&format=png&auto=webp&s=69e421c4e7e0ce7e497f63d698953af54235b3e3
Background: I have 5 years of industry experience as a front end developer. I am about to start a new job as a senior UI developer with a company that is into identity governance and cloud security. I want to learn more about cloud security in order to understand what …
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew
- 🐦 Follow me on Twitter or hire me.








