SRE Weekly Issue #271
📖 [The CloudSecList] Issue 88
[tl;dr sec] #84 - Establishing a Cloud Security Program, Measuring Security
Amazon Macie supports criteria-based bucket selection for sensitive data discovery jobs
Amazon Elastic File System - 2 new methods
Amazon Forecast Service - 1 updated methods
Amazon Lex Model Building V2 - 6 new methods
Building fine-grained authorization using Amazon Cognito, API Gateway, and IAM
AWS Shield threat landscape review: 2020 year-in-review
AWS Verified episode 5: A conversation with Eric Rosenbach of Harvard University’s Belfer Center
How to verify AWS KMS signatures in decoupled architectures at scale
On Establishing a Cloud Security Program




✍️ Just blogged: "🧩 On Establishing a Cloud Security Program 🧩" - Some actionable advice that can be undertaken to establish a #cloud #security program aimed at protecting a cloud native, service provider agnostic, container-based, offering marcolancini.it/2021/blog-clou…
 130
130 51May 18 · 2:32 PM
51May 18 · 2:32 PM
Awhile ago I wrote a blog post tracking how logging could be enabled on 60+ #AWS services. I've gotten a lot of pings about updating the associated CSV, so I'm moving it to GitHub and MIT-licensing it to allow for easy community contributions:
github.com/matthewdfuller…
 95
95 25May 21 · 12:03 AM
25May 21 · 12:03 AM
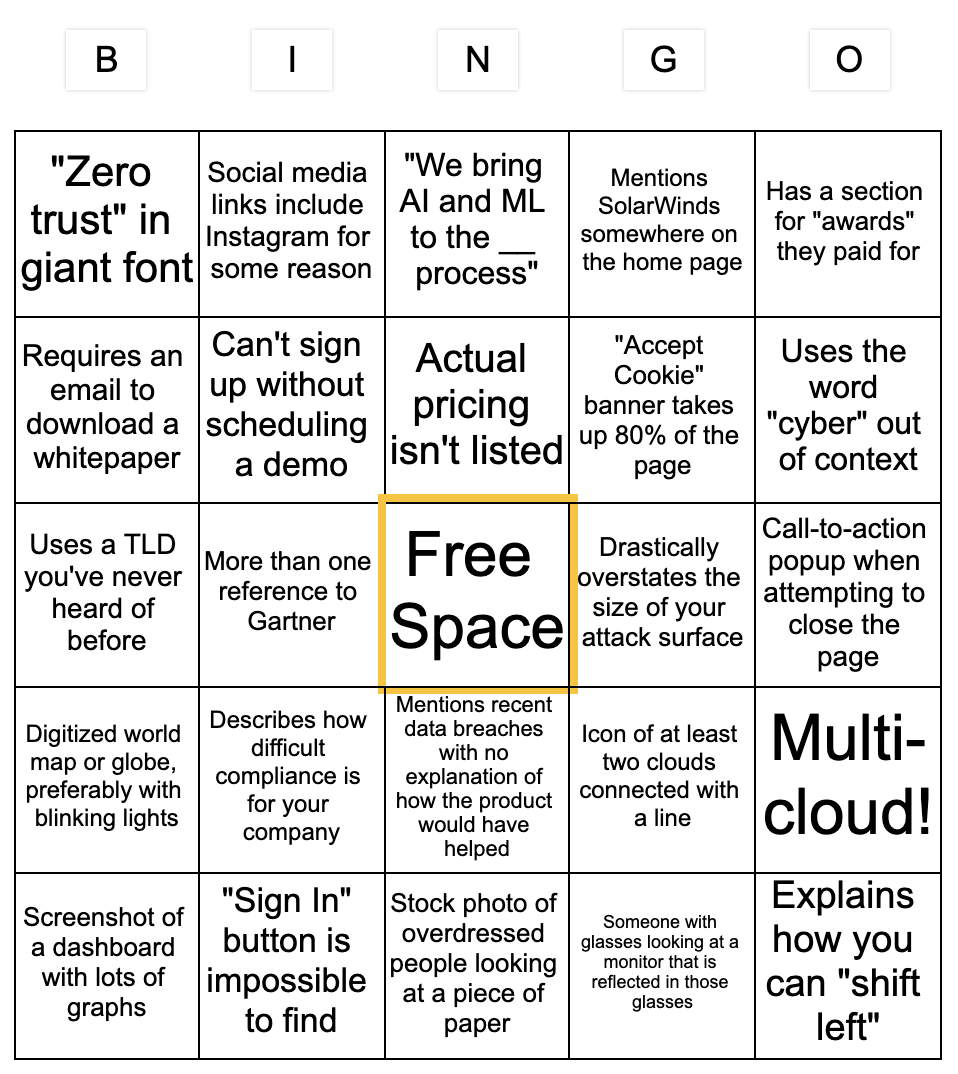
Introducing... Security Vendor Website Bingo!
Did I miss any good ones?
#cloud #security #saas #devops
 60
60 22May 18 · 11:00 PM
22May 18 · 11:00 PM
🔍 How to test Chrome Extensions by @CryptoGangsta
Covers:
* Analyze native app <> extension traffic
* Unpacking, modifying (instrumenting)
* Reverse engineering obfuscated JS
* Dynamic analysis w/ DevTools
* Exporting functions for manual fuzzing
parsiya.net/blog/2021-04-3…
 54
54 22May 18 · 5:00 PM
22May 18 · 5:00 PM
I'm hiring for the cloud security team at Aurora (self-driving vehicles). Someone to help implement zero trust things (such as Istio and OPA) in AWS and someone to help secure CI/CD things. Remote (US), experienced engineers.
aurora.tech/jobs/cloud-sec…
aurora.tech/jobs/cloud-sec…
 53
53 10May 20 · 2:59 AM
10May 20 · 2:59 AM
🦊 FOX - Fix Objective-C XREFs in @GHIDRA_RE
Reversing iOS apps?
Check out @apps3c & @0xdea's Ghidra script that adds XREFs (and potential XREFs) to iOS disassembled and decompiled code
Uses the string arguments passed to `objc_msgSend`
security.humanativaspa.it/fox-fix-object… #redteam
 41
41 13May 17 · 9:00 PM
13May 17 · 9:00 PM
Public SSM docs found by the folks at Checkpoint.
research.checkpoint.com/2021/the-need-… ht @LastWeekinAWS
 30
30 9May 18 · 4:24 AM
9May 18 · 4:24 AM
At Yellowstone. A ton of Buffalo came through my campground. Wild

 33
33 0May 18 · 2:42 AM
0May 18 · 2:42 AM
This weekend was the first time I have had “Brigid Energy” in a long time. Here is my story about how I recharged, what I did for myself, and what we did as a team. (1/15)

 26
26 3May 17 · 10:59 PM
3May 17 · 10:59 PM
Most (all?) of the AWS User Guides have a Troubleshooting section in them (at the end). If I'm going to be using a service a lot, I jump to that section and find out what the most common issues are, saves HEAPS of time e.g. docs.aws.amazon.com/IAM/latest/Use…, docs.aws.amazon.com/lambda/latest/…, etc
 17
17 5May 21 · 11:00 PM
5May 21 · 11:00 PMTalk me off a ledge - I'm a cloud architect trying to switch jobs and I've been passed on 3 jobs by failing coding challenges. Since when are cloud architects "engineers who read about aws?"
I'm currently a senior architect at a major FAANG level (but not one of the fab 5) company. 15 years xp and I have my masters in CS. At my firm, an architect is expected to be involved in major projects and we act as a blend of being an …
Four ways of writing infrastructure-as-code on AWS
I wrote the same app (API Gateway-Lambda-DynamoDB) using four different IaC providers and compared them across.
- AWS CDK
- AWS SAM
- AWS CloudFormation
- Terraform
https://www.notion.so/rxhl/IaC-Showdown-e9281aa9daf749629aeab51ba9296749
What's your preferred way of writing IaC?
IAM Zero: I released a tool which automatically suggests least-privilege IAM policies
A month ago I made a post about IAM Zero, a tool which detects IAM issues and suggests least-privilege policies.
It uses an instrumentation layer to capture AWS API calls and send alerts to a collector - similar to how Sentry, Rollbar, etc capture errors in web applications. The collector …
Difference between Microsoft Azure Security Center and Azure Sentinel
Many Cloud Engineers often fail to get the difference between Azure Security Center (ASC) and Azure Sentinel. These two products look very comparative at first and both are offered by Microsoft to secure your Azure infrastructure to the best of their abilities. There are a few fundamental explanations behind this …
- 🖊️ This newsletter was fwd to you? Subscribe here
- 💌 Want to suggest new content: contact me or reply to this email
- ⚡️ Powered by Mailbrew











