
📣 Sponsor
ProwlerPro is the most comprehensive tool for cloud security. ProwlerPro is trusted by orgs of all sizes, and used everyday so teams can be confident in their cloud security framework.
Sign up for free today for:
- Dashboards with actionable, direct insights for every level of detail of your security posture
- Holistic view of your infrastructure for any AWS region
- Answers in minutes
Use ProwlerPro to see what your first scan discovers.
🐿 In a nutshell
Announcing fwd:cloudsec 2023, the leading independent, community-driven cloud security conference. This event brings together real-world cloud security practitioners to help the community of fellow practitioners achieves world-class security in the cloud.
The conference will take place on June 12-13, 2023, in Los Angeles.
Don't miss out on this opportunity to connect with the best in cloud security.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSConfigMultiAccountSetupPolicy
- AWSIotRoboRunnerFullAccess
- AWSIotRoboRunnerServiceRolePolicy
- AWSMigrationHubOrchestratorServiceRolePolicy
- AdministratorAccess-Amplify
- AmazonCloudWatchRUMServiceRolePolicy
- AmazonGuardDutyServiceRolePolicy
- AmazonInspector2ServiceRolePolicy
- AmazonLaunchWizard_Fullaccess
📊 Pool of the week
Q: Your company policies require encryption of sensitive data at rest. You are considering the possible options for protecting data while storing it at rest on an EBS data volume, attached to an EC2 instance. Which of these options would allow you to encrypt your data at rest?
Past week pool:
Q: The decision was made to place database hosts in their own VPC, and to set up VPC peering to different VPCs containing the application and web tiers. The application servers are unable to connect to the database. Which network troubleshooting steps should be taken to resolve the issue?
Answer: B (17/19 votes) 🎉
🙏 Support
Did you find AWS Security Digest newsletter enjoyable to read?
If so, why not support our next edition by becoming a sponsor?
Additionally, please feel free to share our newsletter with your friends and follow us on Twitter.









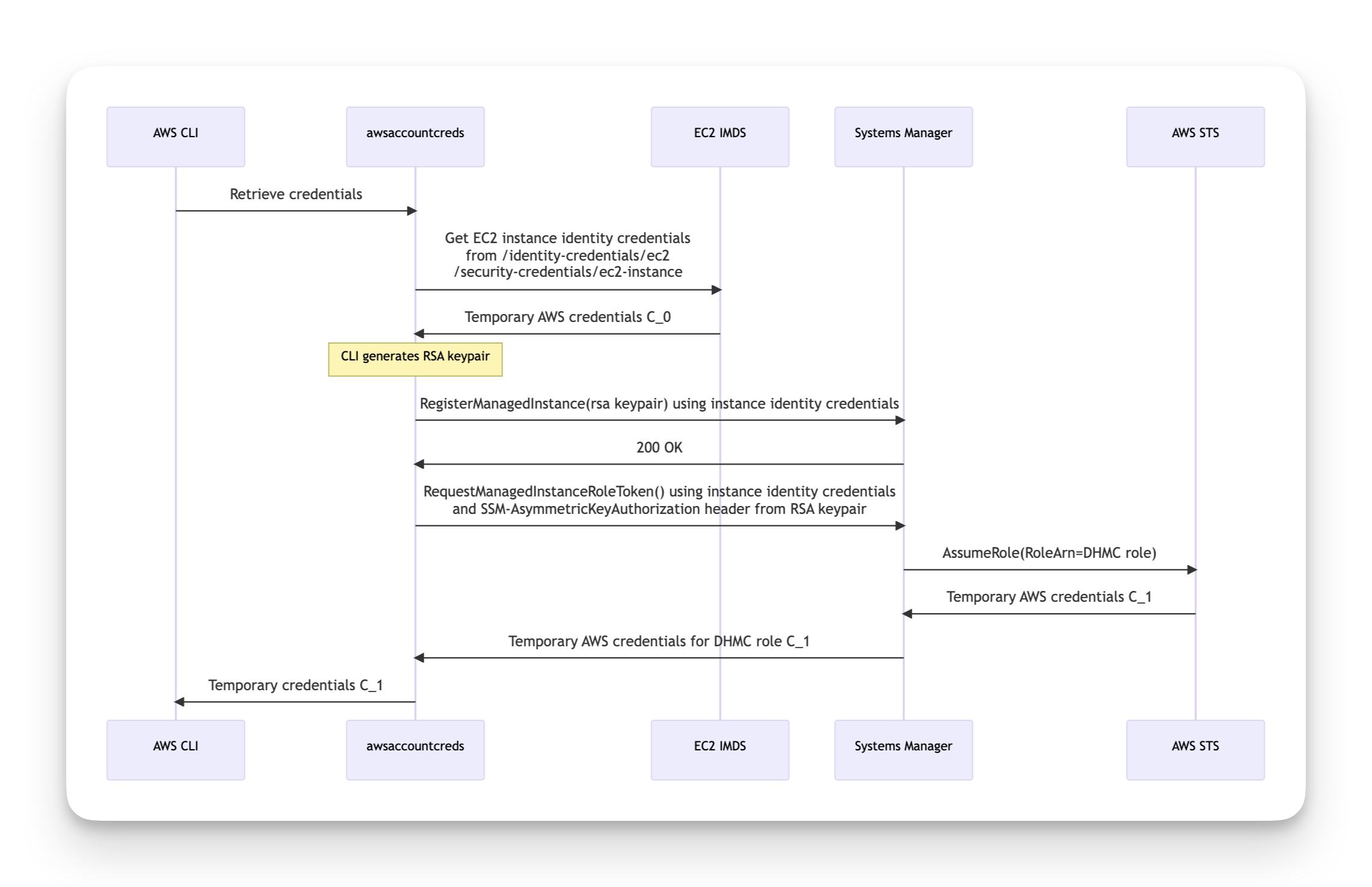






I published a blog post (and PoC CLI) describing how the new Systems Manager Default Host Management Configuration (what a mouthful) provides a new way to pass an IAM role to all EC2 instances in your account+region - even those without instance profiles.
awsteele.com/blog/2023/02/2…
 145
145 33Feb 21 · 12:21 AM
33Feb 21 · 12:21 AM
I am in constant awe of Aidan's ability to quickly jump onto a new feature, figure out how it works, develop a new tool that uses that, write a blog post, and in this case communicate findings to AWS security and create a diagram! This was 75 hours from announcement to all this!

I published a blog post (and PoC CLI) describing how the new Systems Manager Default Host Management Configuration (what a mouthful) provides a new way to pass an IAM role to all EC2 instances in your account+region - even those without instance profiles.
awsteele.com/blog/2023/02/2…

 135
135 10Feb 21 · 4:37 AM
10Feb 21 · 4:37 AM
It’s not S3 ransomware unless it comes from the global region of AWS. Otherwise, it’s just “sparkling bucket encryption events”.
 118
118 24Feb 25 · 3:53 PM
24Feb 25 · 3:53 PM
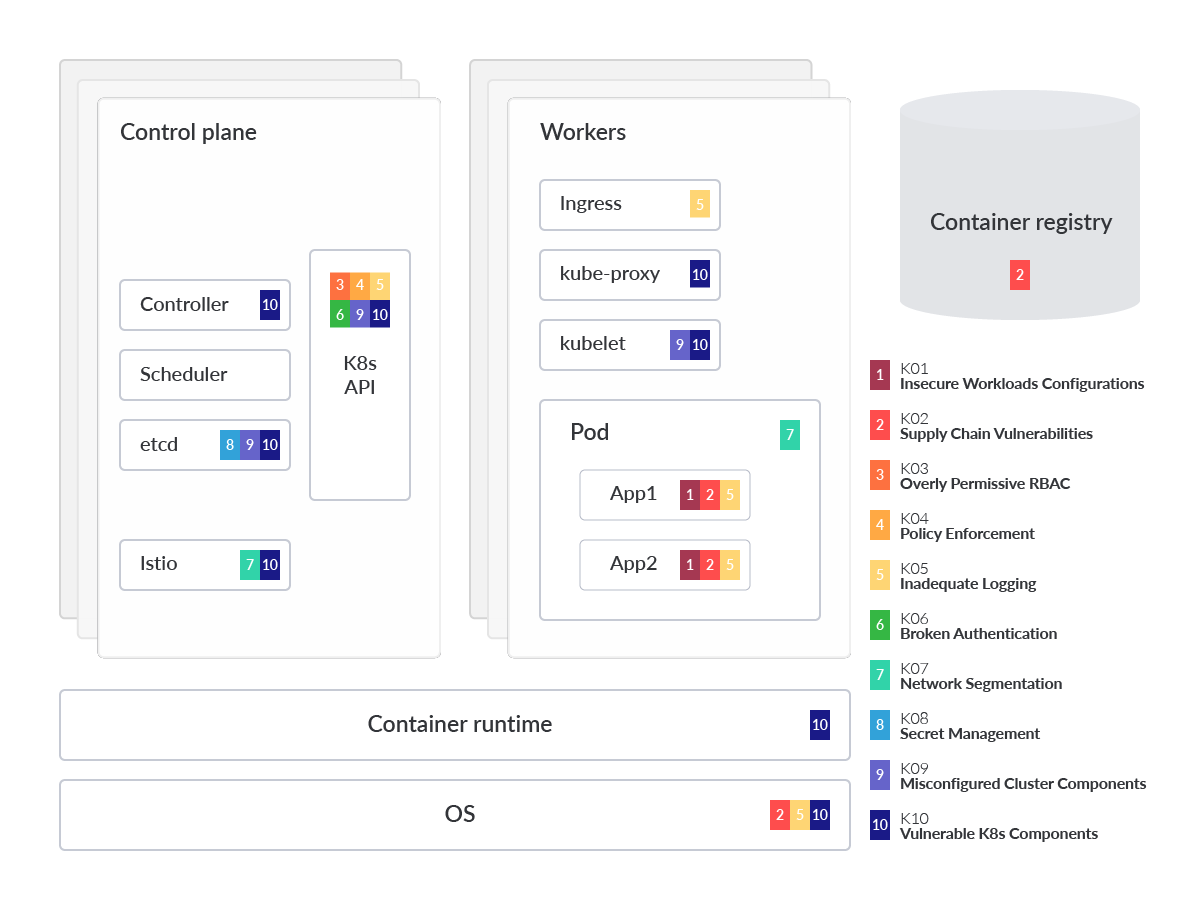
🗒️ @owasp Kubernetes Top 10
Broken down into 3 categories in order of likelihood:
1️⃣ Misconfigurations
2️⃣ Lack of visibility
3️⃣ Vulnerability management
Risks, mitigations, and lots of relevant tools
By @sysdig
sysdig.com/blog/top-owasp…
 83
83 29Feb 22 · 9:00 PM
29Feb 22 · 9:00 PM
Managing IAM resources or building security solutions to monitor them. You will want to read these two blog posts on everything IAM APIs👇
 71
71 12Feb 22 · 5:00 PM
12Feb 22 · 5:00 PM
The latest in prototype pollution 🧵
#bugbounty #bugbountytips
 59
59 17Feb 24 · 5:00 PM
17Feb 24 · 5:00 PM
🎫 Ticket date announcement! 🎫
fwd:cloudsec tickets will be on sale in two batches on Feb 27 11:59AM ET and Feb 27 11:59PM ET!
No inflation here… tickets will continue to be $100 this year.
eventbrite.com/e/556255303587/
 44
44 22Feb 24 · 11:33 PM
22Feb 24 · 11:33 PM
AWS APIs now have at least three methods (let me know which ones I'm missing!) of authentication by asymmetric crypto:
1. SigV4A uses the `Authorization` header with algorithm AWS4-ECDSA-P256-SHA256. The key is derived from the AWS access key.
 55
55 7Feb 21 · 12:10 AM
7Feb 21 · 12:10 AM
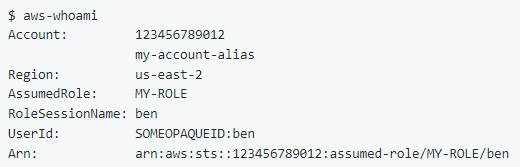
I reimplemented aws-whoami in #golang (from python), so it's a plain binary rather than needing a pip install. It's tidier than plain `aws sts get-caller-identity` (and additionally gets the account name!)—and of course miles better than `aws s3 ls`
github.com/benkehoe/aws-w…
 54
54 5Feb 21 · 2:35 AM
5Feb 21 · 2:35 AM
It's the same with code. Accepting that there's lots of text that needs to exist in your program but will be written by AI, is just categorically worse than evolving programming languages to allow more terse expression
 50
50 5Feb 20 · 6:18 PM
5Feb 20 · 6:18 PMA few months ago my company started moving into building tech. We are fairly new to the tech game, and brought in some developers of varying levels.
Soon after we started, one of the more junior developers pushed live something that seems to have had some AWS keys attached to …
Removed 172.103.41.0/24
- 🖊️ Don't miss out on the latest industry insights - stay ahead of the game by subscribing
- 📢 Gain visibility for your brand by sponsoring our content
- 💌 If you have any suggestions for future topics, let us know









