
📣 Sponsor
Struggling to understand what access people have via AWS Identity Center (SSO)?
We feel your pain…
See what SSO users/groups are effectively admins and which IAM roles they can use with k9’s new Identity Center reporting.
This data is also available in CSV so that you can integrate with your other data in Splunk, Datadog, and Athena.
Start fixing your IAM problems today!
🐿 In a nutshell
Hey Folks,
I hope you enjoyed your weekend!
A recent security report by my friend Christophe @ Datadog revealed a vulnerability in AWS Console that could allow malicious actors to bypass rate limits, leading to unauthorized access.
The issue was fixed by AWS in response to the report – The vulnerability would have allowed attackers to brute force access using well-known passwords lists.
The report serves as a reminder of the importance of constant security monitoring and the need to stay vigilant against potential threats by using CloudTrail and associated alerting.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSApplicationMigrationEC2Access
- AWSBackupServiceRolePolicyForS3Restore
- AWSManagedServices_EventsServiceRolePolicy
- AmazonEKSClusterPolicy
- AmazonElasticMapReduceEditorsRole
- ReadOnlyAccess
📊 Pool of the week
Q: An application team is designing a solution with two applications. The security team wants the applications' logs to be captured in two different places, because one of the applications produces logs with sensitive data. What solution meets the requirement with the LEAST risk and effort?
Past week pool:
Q: From AWS Cert Security Exam sample: A Security Engineer has been informed that a user’s access key has been found on GitHub. The Engineer must ensure that this access key cannot continue to be used, and must assess whether the access key was used to perform any unauthorized activities. What steps must be taken to perform these tasks?
Answer: C (23/30 votes)




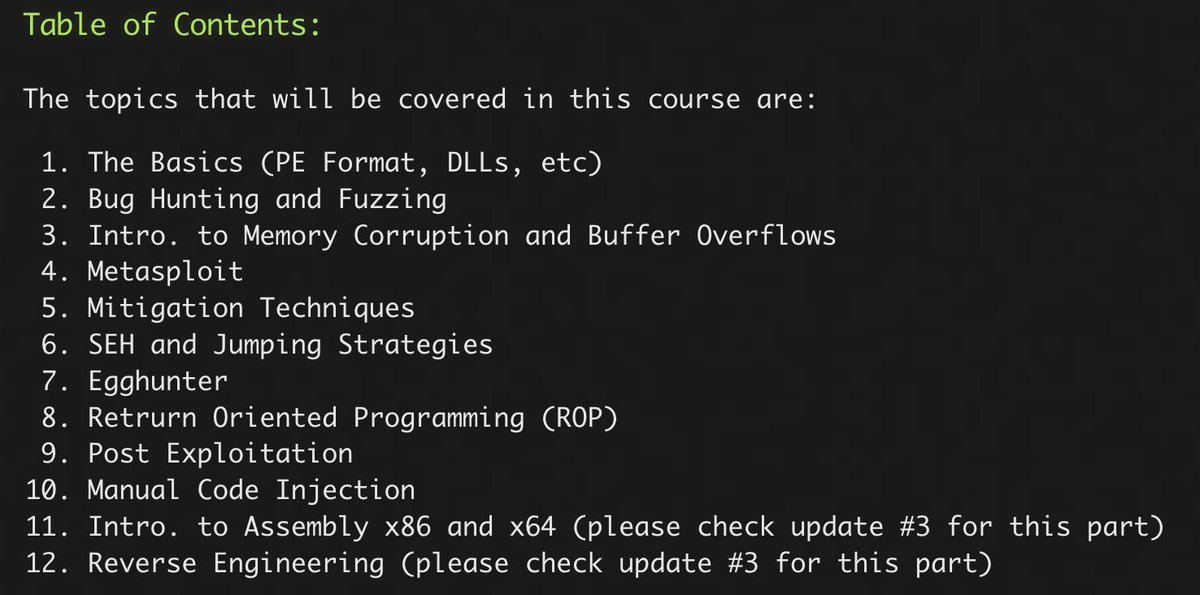
📚 FREE Offensive Security & Reverse Engineering Course
🗒️ Slides
github.com/ashemery/explo…
🧪 Labs
github.com/ashemery/explo…
📺 Videos
youtube.com/playlist?list=…
By @binaryz0ne
#infosec #cybersecurity #pentesting
exploitation.ashemery.com
 775
775 269Feb 07 · 5:00 PM
269Feb 07 · 5:00 PM
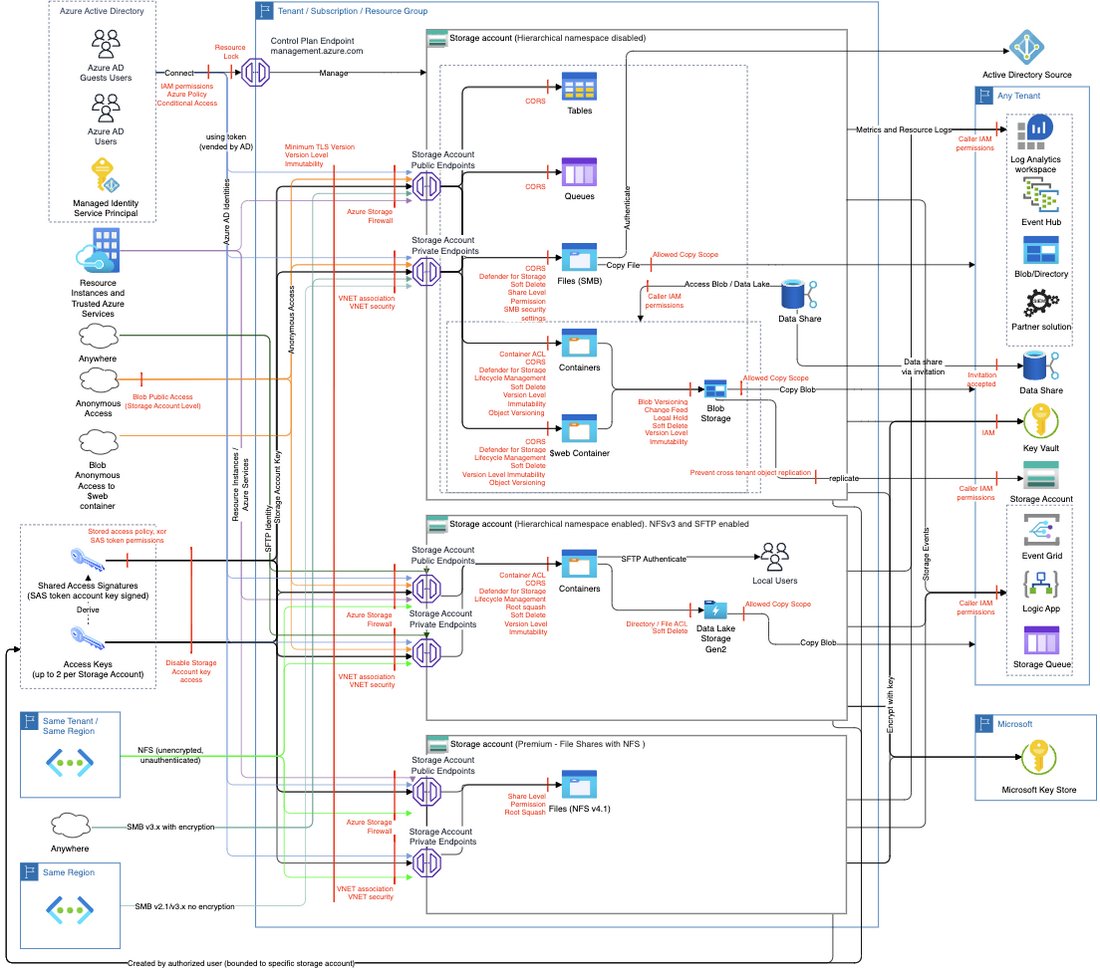
📓 130+ page Threat Model of #Azure Storage
Covers:
1. Best practices (best security/effort ratio)
2. Implementing controls based on your risk tolerance
3. Understanding threats related to a specific feature class
By @trustoncloud
#cloudsecurity
trustoncloud.com/the-last-azure…
 197
197 77Feb 10 · 5:00 PM
77Feb 10 · 5:00 PM
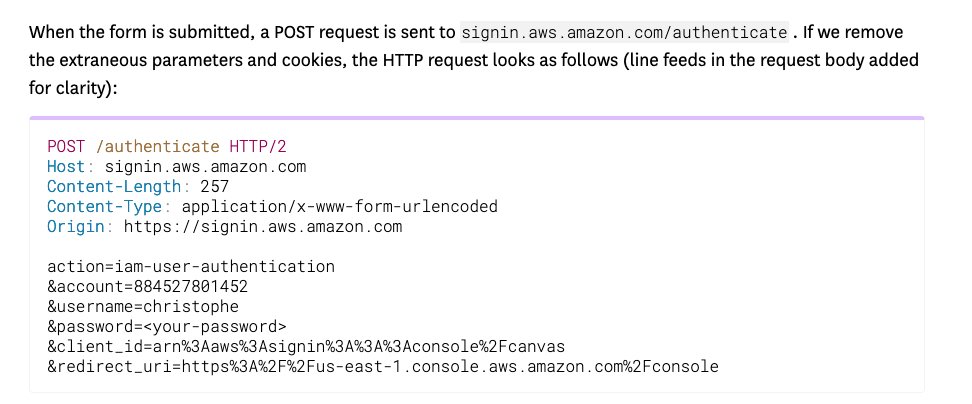
I found a vulnerability in the login rate limiting algorithm of the AWS Console that allowed to continuously brute-force 280 passwords per minute (4.6/second) on a single IAM user without getting blocked
securitylabs.datadoghq.com/articles/aws-c…
Now remediated by AWS, only IAM users without MFA
 167
167 54Feb 06 · 5:59 PM
54Feb 06 · 5:59 PM
I realize I'll never win this battle, but we should stop calling it "infrastructure". It's no longer "infra" (below). It's not something your application is deployed "onto". You have a graph of resources, some (as few as possible) of which have custom code attached.
 144
144 17Feb 07 · 8:37 PM
17Feb 07 · 8:37 PM
New thing: automatic CloudWatch log forwarding across multiple AWS accounts and regions.
No Lambda functions that need maintenance. Just a Kinesis Firehose delivery stream, a Step Function state machine, some EventBridge rules and IAM roles.
github.com/aidansteele/ce…
 77
77 11Feb 13 · 12:34 AM
11Feb 13 · 12:34 AM
Confirmation from AWS of ransomware events targeting data in S3.
Generally good advice but recommending MFA delete in 2023 is bad advice, as it requires the root account (via an access key) to enable it, and the MFA delete functionality can only be used by IAM Users.

The AWS Security, Identity & Compliance Blog #AWSSecurity
aws.amazon.com/blogs/security…
By: Megan O'Neil, Kyle Dickinson and Karthik Ram
 70
70 18Feb 06 · 8:56 PM
18Feb 06 · 8:56 PM
Guess who gets to co-present with @mauilion @IanColdwater and @raesene at KubeCon EU?
I am beyond excited to talk about “Malicious Compliance: Reflections on Trusting Container Scanners” with the best geese in the biz. See you all in Amsterdam!
kccnceu2023.sched.com/event/05d730c6…
 73
73 10Feb 09 · 12:07 PM
10Feb 09 · 12:07 PM
The Wiz State of the Cloud report is out! @AmitaiCo and I put this together using Wiz's visibility to provide some stats. wiz.io/lp/state-of-th…
 56
56 13Feb 07 · 5:09 AM
13Feb 07 · 5:09 AM
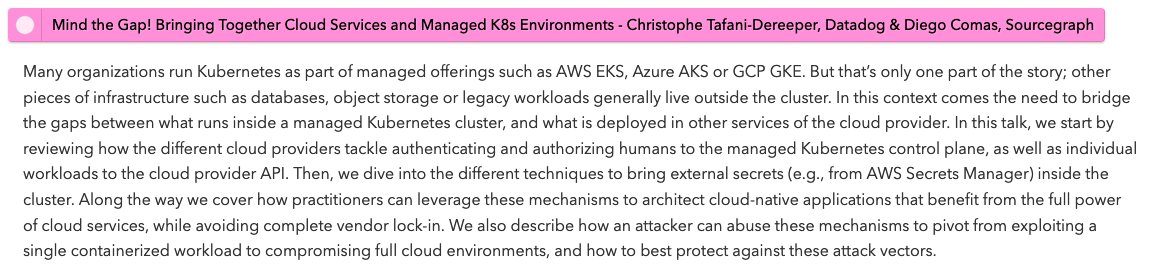
I'll be in Amsterdam this year for my first KubeCon, presenting with @diegocomas how to secure and attack managed Kubernetes environments!
kccnceu2023.sched.com/event/1HyZm/mi…
 40
40 6Feb 09 · 9:11 AM
6Feb 09 · 9:11 AM
I just built a new GitHub Actions deployment pipeline to AWS using OIDC, and wow, it’s so much nicer than dealing with access keys (a bit late to the party, I know).
 40
40 3Feb 10 · 5:37 AM
3Feb 10 · 5:37 AMRemoved 13.34.87.192/26
Added 15.230.187.0/24
- 🖊️ Don't miss out on the latest industry insights - stay ahead of the game by subscribing
- 📢 Gain visibility for your brand by sponsoring our content
- 💌 If you have any suggestions for future topics, let us know








