
🐿 In a nutshell
In this article Teri Radichel explains AWS security responsibilities, which include securing the infrastructure and physical facilities, managing the security of the cloud, providing secure access to customers, and providing security-related services.
Reminder: The customer is responsible for securing their own data, applications, and access control.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSElasticBeanstalkManagedUpdatesCustomerRolePolicy
- AWSElasticBeanstalkManagedUpdatesServiceRolePolicy
- AWSIPAMServiceRolePolicy
- AWSResourceExplorerServiceRolePolicy
- AmazonAthenaFullAccess
- CloudwatchApplicationInsightsServiceLinkedRolePolicy
- Ec2InstanceConnectEndpoint
📊 Pool of the week
Q: What is the maximum number of AccessKey you can generate for a single IAM User?
- 0 (should not be used :))
- 1
- 2
- Unlimited
Past week pool: What is the maximum number of IAM policies (in-line) that can be attached to a single IAM role? 100 / 50 / Unlimited
Answer: You can use as many inline policies as you want, but the aggregate policy size can't exceed the character quotas. The inline policy character limits are 2,048 for users, 10,240 for roles, and 5,120 for groups.

My talk "What I Wish I Knew Before Pentesting AWS Environments" for SANS Pen Test Hackfest 2022 is now on YouTube! Check it out if you're interested in learning more ways to attack AWS environments.
youtube.com/watch?v=jq8SAF…
 93
93 30Jan 24 · 5:06 PM
30Jan 24 · 5:06 PM
🔑 FIDO2, New Hires & Lost Keys
Part 3/3 in @PalantirTech's Passwordless AuthN Series
➡️ How they handle the "chicken and egg" new FIDO2 user problem (Azure TAP codes) and when users lose keys
blog.palantir.com/new-hires-lost…
 52
52 13Jan 27 · 9:00 PM
13Jan 27 · 9:00 PM
I've seen it pointed out that ChatGPT (et al) has shown that the science fiction has gotten it very wrong when it comes what AI will be like. I demand a reboot of Star Trek TNG where Data is an epic bullshitter with no regard for the truth and a very poor grasp of arithmetic
 55
55 9Jan 26 · 8:45 PM
9Jan 26 · 8:45 PM
What's the fattest Docker image you've seen in the wild?
 59
59 2Jan 26 · 1:05 AM
2Jan 26 · 1:05 AM
The hardest part of serverless is giving up control. Everyone says it's good to update your dependencies and runtime versions. It's a *good* thing to be forced to do that. 1/3
 52
52 2Jan 25 · 10:18 PM
2Jan 25 · 10:18 PM
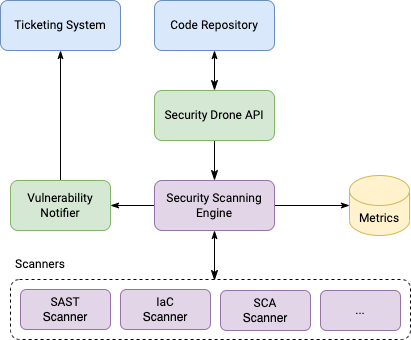
📈 Security Drone: Scaling Continuous Security at Revolut
* Scan every PR
* Use Kubernetes cluster to scan independently of CI/CD pipelines
🛠️ Tools: Semgrep for SAST, Snyk for SCA, Checkov for IaC
~3.8% FP rate for SAST!
medium.com/revolut/securi…
 38
38 13Jan 23 · 11:00 PM
13Jan 23 · 11:00 PM@kmcquade3 Don't shame docker images. All containers are beautiful
 35
35 2Jan 26 · 2:31 AM
2Jan 26 · 2:31 AM
This is a powerful concept wherein given that Wiz is already scanning disk snapshots for vulnerable libraries and malware, it can also scan for application and OS misconfigurations, including custom checks you create, without a performance impact to the running servers.

Say goodbye to tedious config management tasks! Wiz's agentless custom host rules revolutionize the way you manage your infrastructure. No agents or manual commands needed. Create your own rule logic for full coverage across your cloud estate. Learn more: wiz.io/blog/streamlin…
 25
25 7Jan 26 · 7:50 PM
7Jan 26 · 7:50 PM
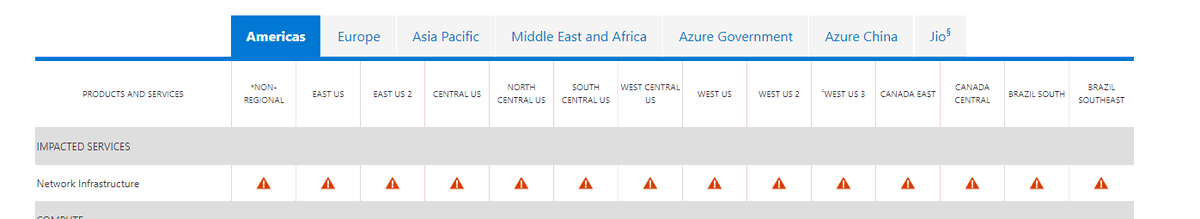
Wow, global Azure outage? My money is on BGP 👀

Updated #azure problems with network outages now in status portal affecting network infrastructure in all regions
 23
23 3Jan 25 · 9:34 AM
3Jan 25 · 9:34 AMI messed up and saved a 500k max wcu for provisioned dynamodb setting. I realized it 5 min after and immediately deleted the table. The estimated monthly cost is 278k and hourly 1.5k. Will I get charged for 1.5k even though I deleted the table 5 min later? I think …
Added 13.34.89.64/26
Added 13.34.89.128/26
Added 13.34.89.192/26
- 🖊️ Don't miss out on the latest industry insights - stay ahead of the game by subscribing
- 📢 Gain visibility for your brand by sponsoring our content
- 💌 If you have any suggestions for future topics, let us know










