
Sponsor
unusd.cloud helps you reduce your environmental impact 🍃 by identifying and shutting down mistakenly active assets, lowering your security risks 🔒, and decreasing your AWS bills 🗒️.
Don’t let unused assets drain your AWS budget.
It's free (forever) for a single AWS Account.
In a nutshell
From last week: AWS just made security a top priority by default. S3 now automatically encrypts all new objects with SSE-S3. This change puts another security best practice into effect automatically, with no impact on performance & no action required on your side. Existing buckets using S3 default encryption will not change.
📢 MAMIP (Monitor AWS Managed IAM Policies)
Policies changed since last week:
- AWSCleanRoomsFullAccess
- AWSCleanRoomsFullAccessNoQuerying
- AWSCleanRoomsReadOnlyAccess
- AWSHealth_EventProcessorServiceRolePolicy
- AWSServiceCatalogAdminFullAccess
- AWSSupportServiceRolePolicy
- AmazonLaunchWizard_Fullaccess
- AmazonSageMakerNotebooksServiceRolePolicy
- ReadOnlyAccess




the call i'm on just called a floppy disk "the save icon" and i guess i'll go die of old age now
 413
413 30Jan 12 · 4:28 PM
30Jan 12 · 4:28 PM
✅ How to *actually* roll out YubiKeys/WebAuthN
Industry advice is to "just do it"
But it's actually really hard in practice
8 resources on lessons learned from companies who've done it 🧵
 266
266 60Jan 11 · 5:00 PM
60Jan 11 · 5:00 PM
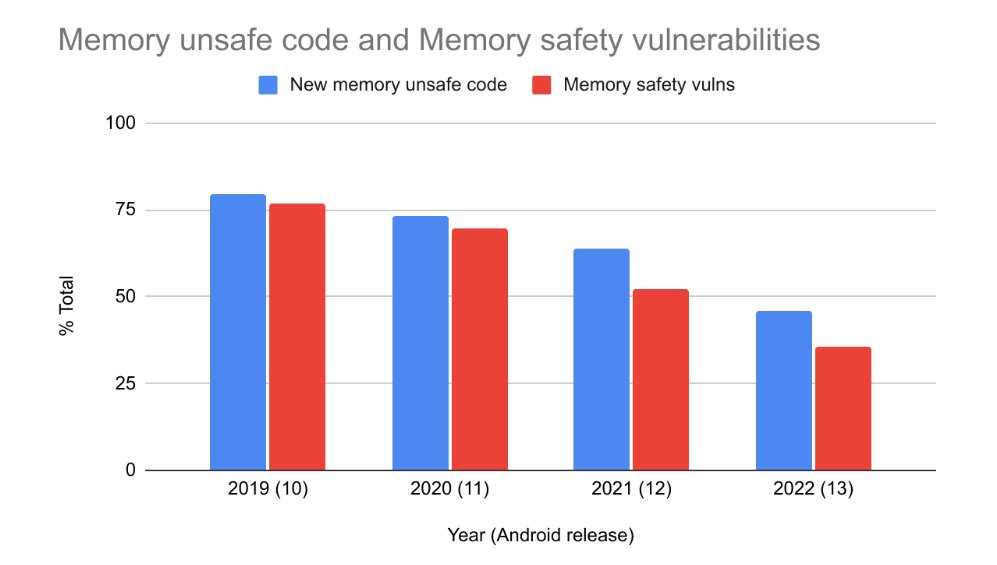
🦀 Memory Safe Languages in Android 13
To date, 0 memory safety vulns in Android’s Rust code
Historical vulnerability density is >1/kLOC in C/C++ components → Rust has already prevented 100s of vulns
By @jeffvanderstoep
security.googleblog.com/2022/12/memory…
 117
117 27Jan 09 · 5:00 PM
27Jan 09 · 5:00 PM
My neighbor works in finance and is required to take a minimum amount of no-contact PTO every year. It ensures there's organizational resilience and it's even seen as a check on fraud. Unlimited PTO would be better with measures like that included ... enforce a minimum.

FTR, unlimited PTO is a scam and we all know it.
 113
113 7Jan 12 · 10:37 PM
7Jan 12 · 10:37 PM
If you're interested in permissions management and authorization, check out my new blog post on the new Cedar language - currently integrated into Amazon Verified Permissions and #AWS Verified Access, and more in the future. 🌲🔐
onecloudplease.com/blog/cedar-a-n…
 87
87 25Jan 11 · 9:34 AM
25Jan 11 · 9:34 AM
How many different AWS phishing vectors are you aware of?
I found four - anything I missed?
ramimac.me/aws-phishing
 88
88 22Jan 09 · 7:46 PM
22Jan 09 · 7:46 PM
Do you work somewhere that uses Github Enterprise Cloud, but doesn't use GitHub Actions OIDC because it's not possible for AWS org admins to lock down role creation to only your GitHub Enterprise?
I wrote this for you. ✨Fancy✨ screenshot for the tl;dr
awsteele.com/blog/2023/01/1…

 52
52 11Jan 11 · 5:34 AM
11Jan 11 · 5:34 AM
A good example of threat lists in CI/CD: storage.googleapis.com/prd-engineerin…
This 👆 is part of the worth-reading article: engineering.mercari.com/en/blog/entry/… by @MercariDev
 35
35 10Jan 10 · 9:42 AM
10Jan 10 · 9:42 AM
“Just use Kubernetes” 🙄

@dhh Running your own infra on your own metal has never been easier! Just use Kubernetes. You can find a better open sourced version of practically every AWS product. Even Lambdas
 39
39 5Jan 13 · 8:47 PM
5Jan 13 · 8:47 PMPersonally, it drives me up the wall. I feel like 9/10 times a post from /r/aws ends up in my front page, it's just a link to an article with zero comments, no discussion to be had, etc.
I'd feel a lot better about these sorts of posts if the …
Added 15.230.19.250/31
Removed 13.34.81.64/26
- 🖊️ This digest was forwarded to you? Subscribe here
- 📢 Promote your content with sponsorship
- 💌 Want to suggest new content: contact me or reply to this email














